We Download the files and then use the RsaCtfTool to dump the keys:
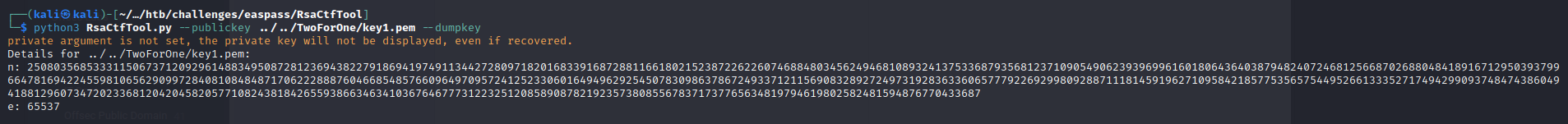
python3 RsaCtfTool.py --publickey ../../TwoForOne/key1.pem --dumpkey
python3 RsaCtfTool.py --publickey ../../TwoForOne/key2.pem --dumpkey
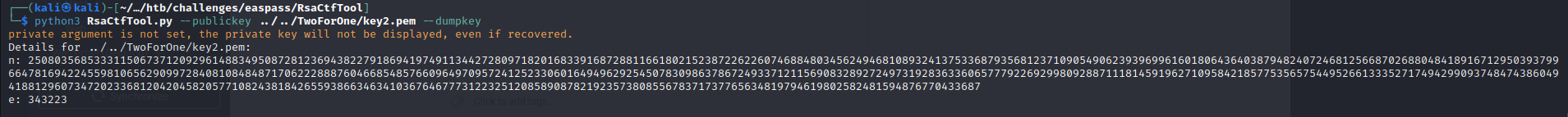
n represents the modulus for the public and private keys
e represents the public key exponent
Both n values are equal between the two keys which is strange.
This means the key is vulnerable to a Common Modulus Attack. Someone wrote a script for this:
https://github.com/HexPandaa/RSA-Common-Modulus-Attack
python3 rsa-cm.py -c1 ../message1 -c2 ../message2 -k1 ../key1.pem -k2 ../key2.pem
We run the script and get the flag:

HTB{C0mmon_M0dUlu5S_1S_b4D}